Question: This problem involves a bias in the key-stream output of RC4. The key-scheduling algorithm and a) Compute the second key-stream byte of the output when
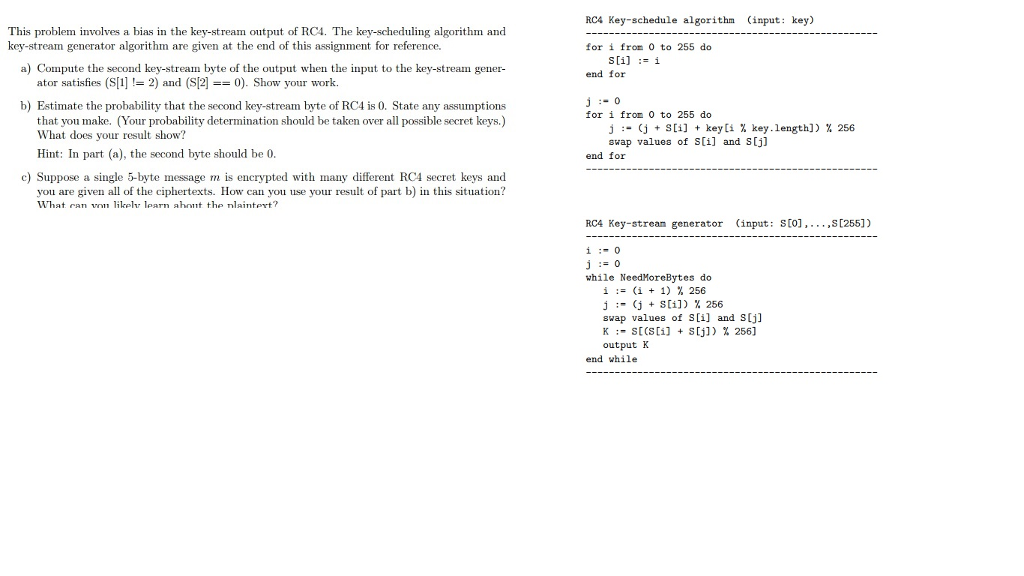
This problem involves a bias in the key-stream output of RC4. The key-scheduling algorithm and a) Compute the second key-stream byte of the output when the input to the key-stream gener- b) Estimate the probability that the second key-stream byte of RC4 is 0. State any assumptions RC4 Key-schedule algorithm (input: key) for i fro O to 255 do end for key-stream generator algorithm are given at the end of this assignment for reference S[i] i ator satisfies (S1-2) and (S12]-0). Show your work. for i fron 0 to 255 do that you make. (Your probability determination should be taken over all possible secret keys.) What does your result show? Hint: In part (a), the second byte should be 0 j :_ (j + S [1] + key [i % key. length]) % 256 swap values of S[i] and Sj] end for c) Suppose a single 5-byte message m is encrypted with many different RC4 secret keys and you are given all of the ciphertexts. How can you use your result of part b) in this situation? RC4 Key-strean generator (input: sto],..,st2551) while NeedMoreBytes do i:= (i + 1) % 256 j :" (j + S[1]) % 256 swap values of S[i] and S[j] K :" S[CS [1] + S [j]) % 256] output K end while This problem involves a bias in the key-stream output of RC4. The key-scheduling algorithm and a) Compute the second key-stream byte of the output when the input to the key-stream gener- b) Estimate the probability that the second key-stream byte of RC4 is 0. State any assumptions RC4 Key-schedule algorithm (input: key) for i fro O to 255 do end for key-stream generator algorithm are given at the end of this assignment for reference S[i] i ator satisfies (S1-2) and (S12]-0). Show your work. for i fron 0 to 255 do that you make. (Your probability determination should be taken over all possible secret keys.) What does your result show? Hint: In part (a), the second byte should be 0 j :_ (j + S [1] + key [i % key. length]) % 256 swap values of S[i] and Sj] end for c) Suppose a single 5-byte message m is encrypted with many different RC4 secret keys and you are given all of the ciphertexts. How can you use your result of part b) in this situation? RC4 Key-strean generator (input: sto],..,st2551) while NeedMoreBytes do i:= (i + 1) % 256 j :" (j + S[1]) % 256 swap values of S[i] and S[j] K :" S[CS [1] + S [j]) % 256] output K end while
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


