Question: Token only components are components that contain the token and do not contain PAN or SAD. True False In a tokenization system, the card data
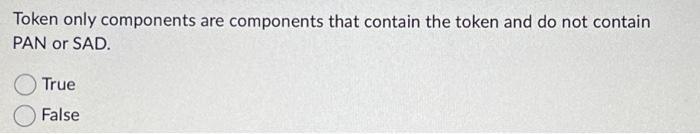
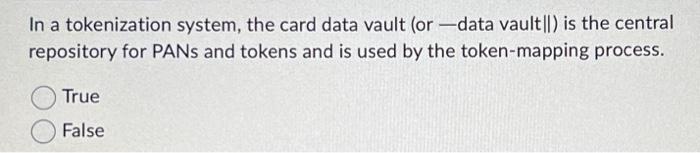
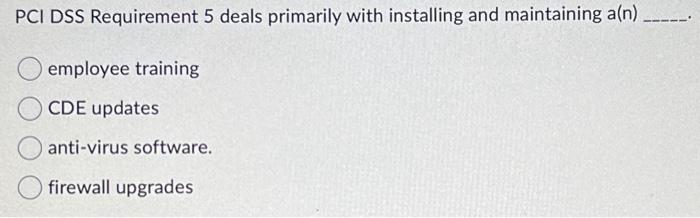
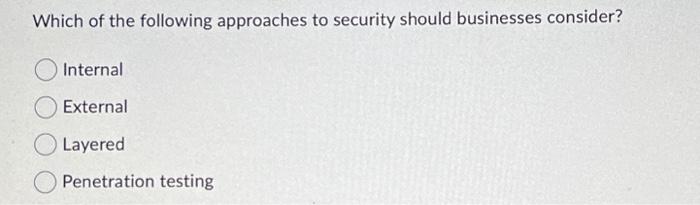



Token only components are components that contain the token and do not contain PAN or SAD. True False In a tokenization system, the card data vault (or - data vault||) is the central repository for PANs and tokens and is used by the token-mapping process. True False PCI DSS Requirement 5 deals primarily with installing and maintaining a(n) employee training CDE updates anti-virus software. firewall upgrades Which of the following approaches to security should businesses consider? Internal External Layered Penetration testing Verifying the effectiveness of a tokenization implementation is not necessary and does not include confirming that PAN is not retrievable from any system component removed from the scope of PCI DSS. True False The processes used to create, use, manage, and protect cryptographic keys that are used to protect PAN data fall under cryptographic key management. True False Only identified users and system components should be allowed access to the tokenization system and tokenization/de-tokenization processes. True False Token only components are components that contain the token and do not contain PAN or SAD. True False In a tokenization system, the card data vault (or - data vault||) is the central repository for PANs and tokens and is used by the token-mapping process. True False PCI DSS Requirement 5 deals primarily with installing and maintaining a(n) employee training CDE updates anti-virus software. firewall upgrades Which of the following approaches to security should businesses consider? Internal External Layered Penetration testing Verifying the effectiveness of a tokenization implementation is not necessary and does not include confirming that PAN is not retrievable from any system component removed from the scope of PCI DSS. True False The processes used to create, use, manage, and protect cryptographic keys that are used to protect PAN data fall under cryptographic key management. True False Only identified users and system components should be allowed access to the tokenization system and tokenization/de-tokenization processes. True False
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


