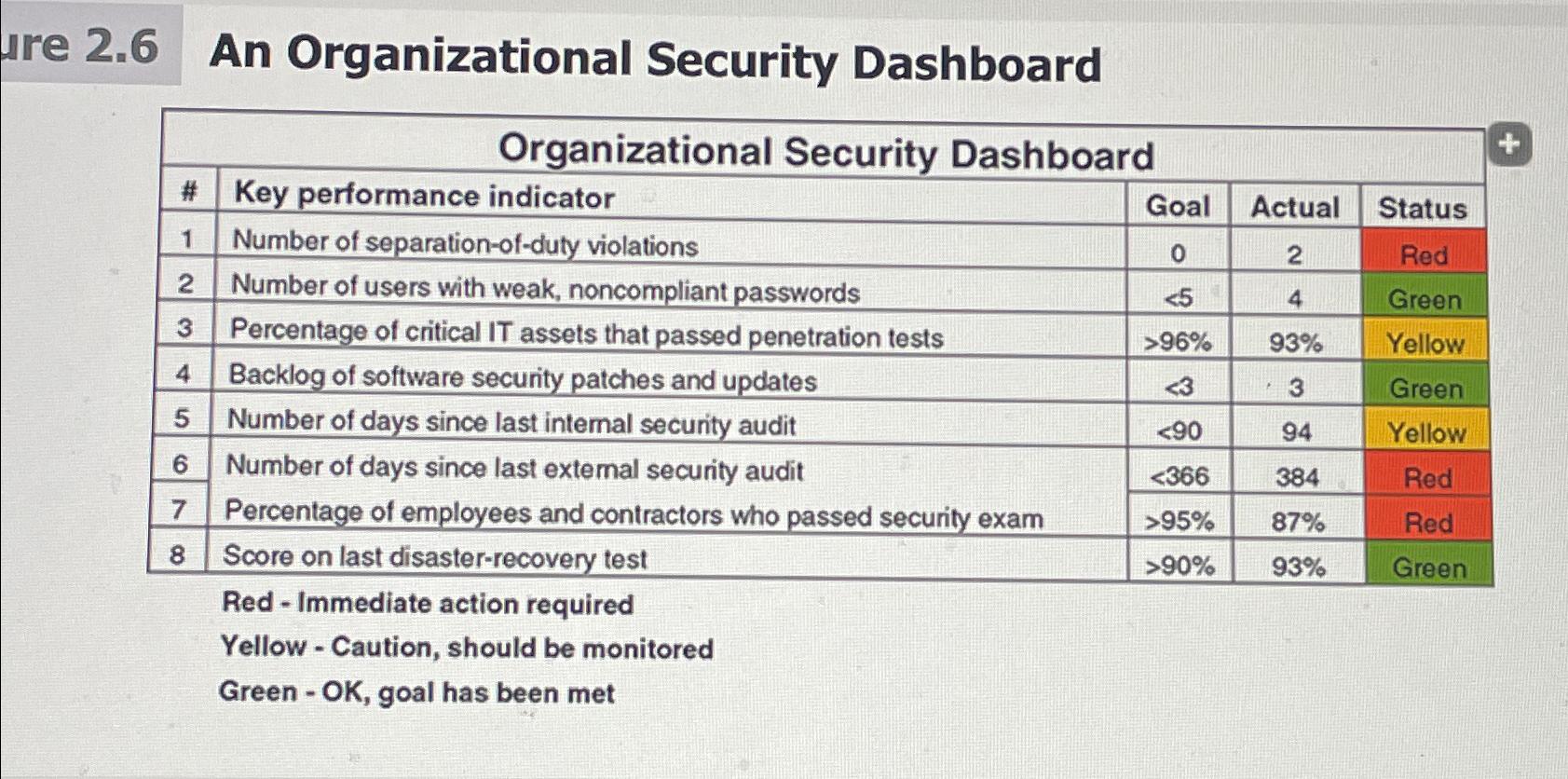
Question: Use Table 2 . 6 to conduct a security self - assessment. Identify specific follow - up actions you need to take.ure 2 . 6
Use Table to conduct a security selfassessment. Identify specific followup actions you need to take.ure An Organizational Security Dashboard
tableOrganizational Security Dashboard#Key performance indicator,Goal,Actual,StatusNumber of separationofduty violations,RedNumber of users with weak, noncompliant passwords,GreenPercentage of critical IT assets that passed penetration tests,YellowBacklog of software security patches and updates,GreenNumber of days since last intemal security audit,YellowNumber of days since last extemal security audit,RedPercentage of employees and contractors who passed security exam,RedScore on last disasterrecovery test,Green
Red Immediate action required
Yellow Caution, should be monitored
Green OK goal has been met
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


