Question: using Python programming language This project is based on a simple jpeg to bmp format conversion open source code called 'jpg2bmp.cpp. I modified it in
using Python programming language
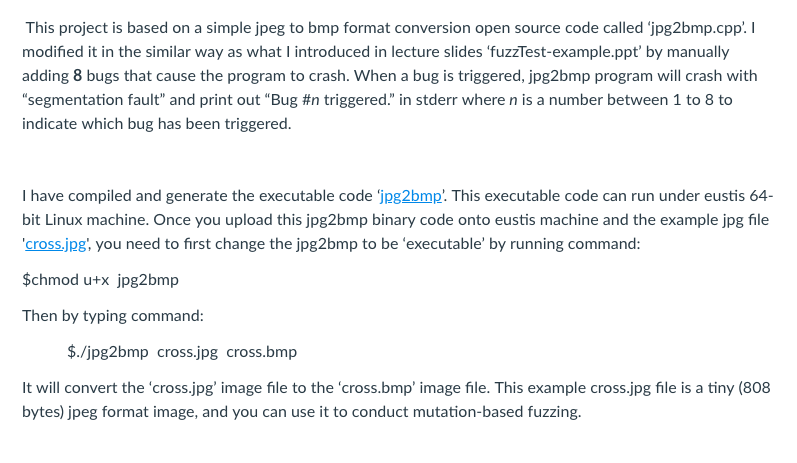
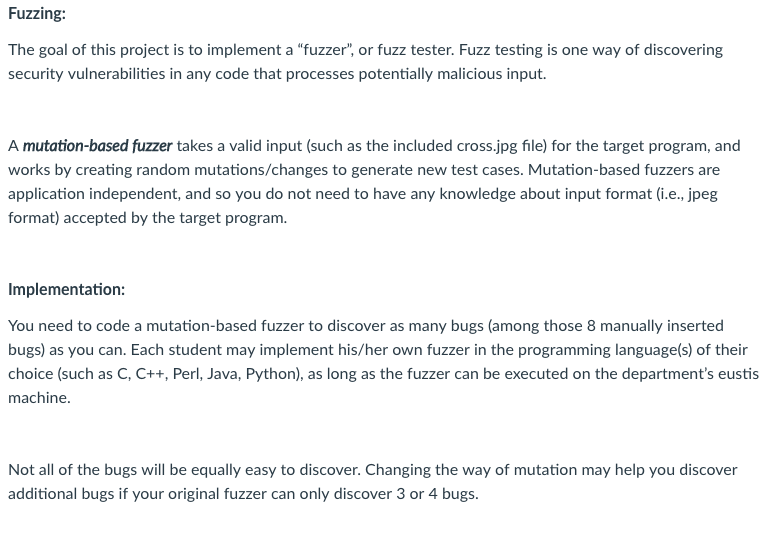
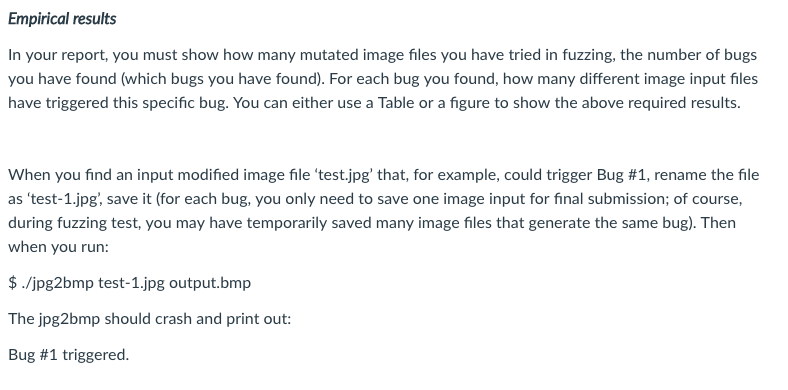
This project is based on a simple jpeg to bmp format conversion open source code called 'jpg2bmp.cpp. I modified it in the similar way as what I introduced in lecture slides fuzzTest-example.ppt' by manually adding 8 bugs that cause the program to crash. When a bug is triggered, jpg2bmp program will crash with "segmentation fault" and print out "Bug #n triggered." in stderr where n is a number between 1 to 8 to indicate which bug has been triggered. I have compiled and generate the executable code jpg2bmp. This executable code can run under eustis 64 bit Linux machine. Once you upload this jpg2bmp binary code onto eustis machine and the example jpg file cross.jpg, you need to first change the jpg2bmp to be 'executable' by running command $chmod utx jpg2bmp Then by typing command: $./jpg2bmp cross.jpg cross.bmp It will convert the 'cross.jpg image file to the 'cross.bmp' image file. This example cross.jpg file is a tiny (808 bytes) jpeg format image, and you can use it to conduct mutation-based fuzzing. Fuzzing: The goal of this project is to implement a "fuzzer", or fuzz tester. Fuzz testing is one way of discovering security vulnerabilities in any code that processes potentially malicious input. A mutation-based fuzzer takes a valid input (such as the included cross.jpg file) for the target program, and works by creating random mutations/changes to generate new test cases. Mutation-based fuzzers are application independent, and so you do not need to have any knowledge about input format (i.e., jpeg format) accepted by the target progranm Implementation You need to code a mutation-based fuzzer to discover as many bugs (among those 8 manually inserted bugs) as you can. Each student may implement his/her own fuzzer in the programming language(s) of their choice (such as C, C++,Perl, Java, Python), as long as the fuzzer can be executed on the department's eustis machine Not all of the bugs will be equally easy to discover. Changing the way of mutation may help you discover additional bugs if your original fuzzer can only discover 3 or 4 bugs. This project is based on a simple jpeg to bmp format conversion open source code called 'jpg2bmp.cpp. I modified it in the similar way as what I introduced in lecture slides fuzzTest-example.ppt' by manually adding 8 bugs that cause the program to crash. When a bug is triggered, jpg2bmp program will crash with "segmentation fault" and print out "Bug #n triggered." in stderr where n is a number between 1 to 8 to indicate which bug has been triggered. I have compiled and generate the executable code jpg2bmp. This executable code can run under eustis 64 bit Linux machine. Once you upload this jpg2bmp binary code onto eustis machine and the example jpg file cross.jpg, you need to first change the jpg2bmp to be 'executable' by running command $chmod utx jpg2bmp Then by typing command: $./jpg2bmp cross.jpg cross.bmp It will convert the 'cross.jpg image file to the 'cross.bmp' image file. This example cross.jpg file is a tiny (808 bytes) jpeg format image, and you can use it to conduct mutation-based fuzzing. Fuzzing: The goal of this project is to implement a "fuzzer", or fuzz tester. Fuzz testing is one way of discovering security vulnerabilities in any code that processes potentially malicious input. A mutation-based fuzzer takes a valid input (such as the included cross.jpg file) for the target program, and works by creating random mutations/changes to generate new test cases. Mutation-based fuzzers are application independent, and so you do not need to have any knowledge about input format (i.e., jpeg format) accepted by the target progranm Implementation You need to code a mutation-based fuzzer to discover as many bugs (among those 8 manually inserted bugs) as you can. Each student may implement his/her own fuzzer in the programming language(s) of their choice (such as C, C++,Perl, Java, Python), as long as the fuzzer can be executed on the department's eustis machine Not all of the bugs will be equally easy to discover. Changing the way of mutation may help you discover additional bugs if your original fuzzer can only discover 3 or 4 bugs
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


