Question: Using the above information, please analyze each protocol (i to v) sent from Alice to Bob in terms of what the protocol is doing, and
Using the above information, please analyze each protocol (i to v) sent from Alice to Bob in terms of what the protocol is doing, and its security level and/or threats, and remedies to secure them.
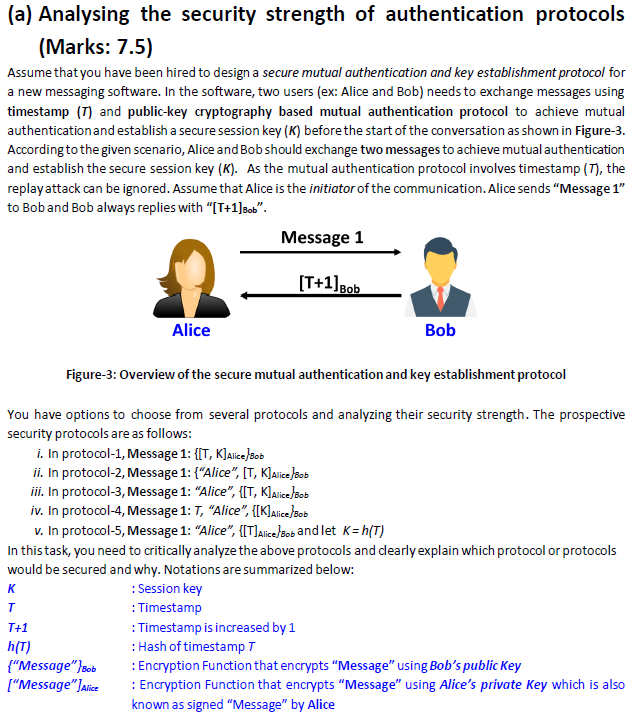
(a) Analysing the security strength of authentication protocols (Marks: 7.5) Assume that you have been hired to design a secure mutual authentication and key establishment protocol for a new messaging software. In the software, two users (ex: Alice and Bob) needs to exchange messages using timestamp (T) and public-key cryptography based mutual authentication protocol to achieve mutual authentication and establish a secure session key (K) before the start of the conversation as shown in Figure-3. According to the given scenario, Alice and Bob should exchange two messages to achieve mutual authentication and establish the secure session key (K). As the mutual authentication protocol involves timestamp (T) ), the replay attack can be ignored. Assume that Alice is the initiator of the communication. Alice sends "Message 1 " to Bob and Bob always replies with " [T+1]Bob ". Figure-3: Overview of the secure mutual authentication and key establishment protocol You have options to choose from several protocols and analyzing their security strength. The prospective security protocols are as follows: i. In protocol-1, Message 1:{[T,K]Alice}Bob ii. In protocol-2, Message 1: {"Alice",[T,K]Alice}Bob iii. In protocol-3, Message 1: "Alice", {[T,K]Alice}Bob iv. In protocol-4, Message 1: T, "Alice", {[K]Alice}Bob v. In protocol-5, Message 1: "Alice", {[T]Alice}Bob and let K=h(T) In this task, you need to critically analyze the above protocols and clearly explain which protocol or protocols would be secured and why. Notations are summarized below: KTT+1h(T){"Message"}Bob["Message"]Alice:Sessionkey:Timestamp:Timestampisincreasedby1:HashoftimestampT:EncryptionFunctionthatencrypts"Message"usingBobspublicKey:EncryptionFunctionthatencrypts"Message"usingAlicesprivateKeywhichisalsoknownassigned"Message"byAlice
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


