Question: Using the values for protocol numbers and port numbers listed in the attached tables (1 & 2) and the packet filtering rules listed in an
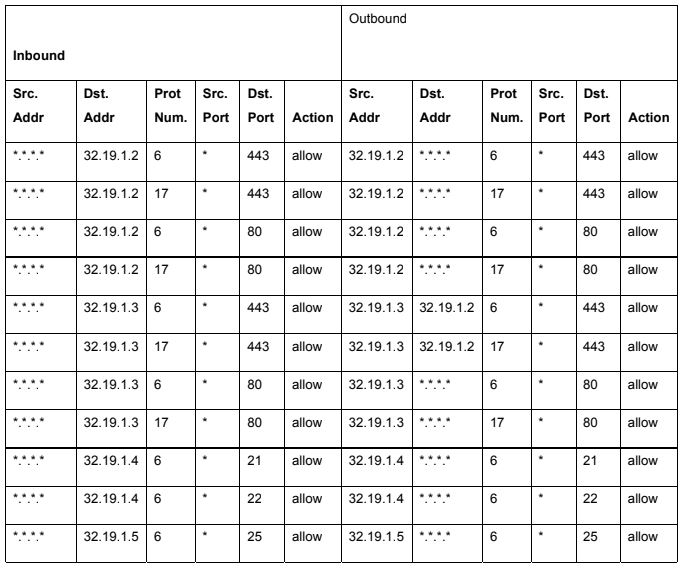
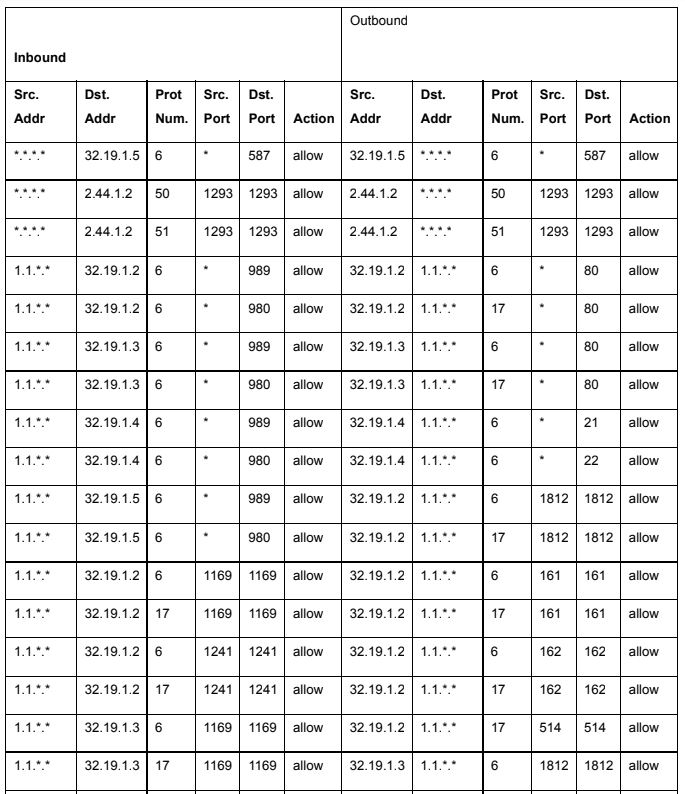
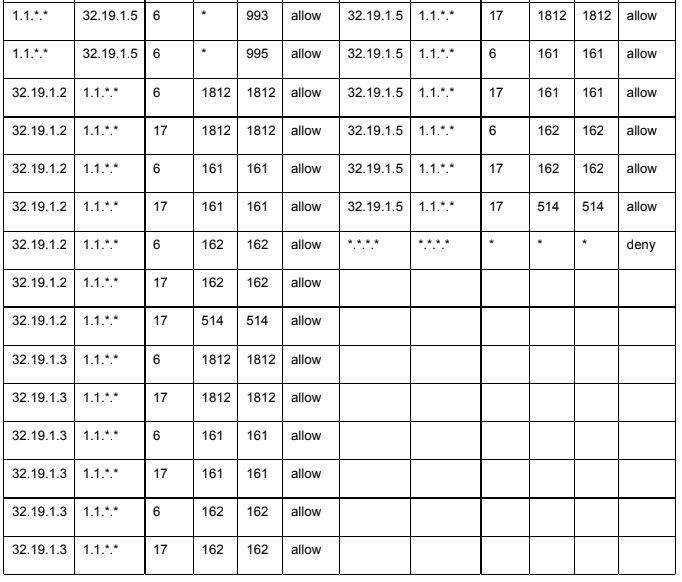
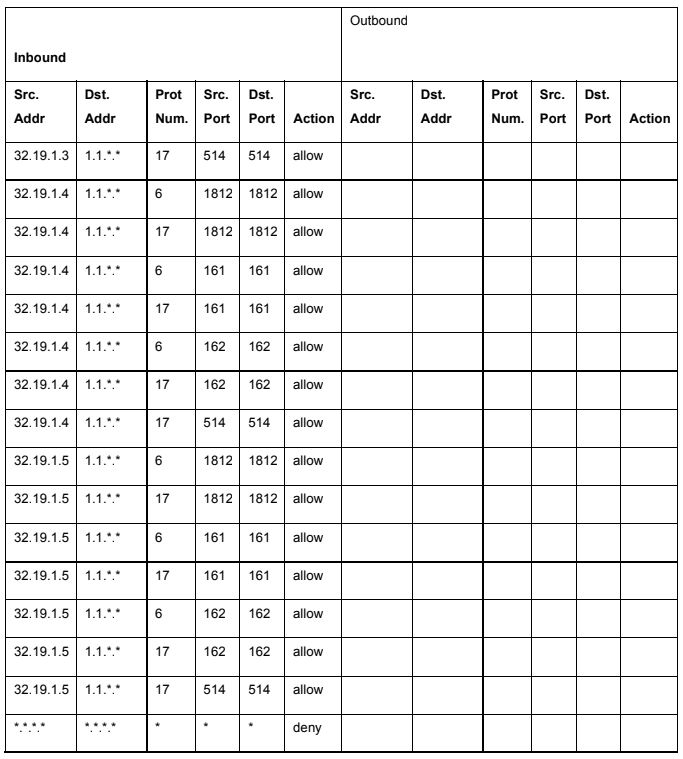
Using the values for protocol numbers and port numbers listed in the attached tables (1 & 2) and the packet filtering rules listed in an attached table (3.1 - 3.4), answer the following (answers should identify the name of the Transport protocol and Application protocol, not the associated numbers!)
1A. What application protocols should be allowed to enter from the Internet (as part of sessions initiated from the Internet) through the DMZ outside router-firewall and reach the servers within the DMZ?
1B. What application protocols should be allowed to enter from the Internet (as part of sessions initiated from the Internet) through the DMZ outside router-firewall and reach the DMZ inside router-firewall?
1C. What application protocols should be allowed to enter from the DMZ inside router-firewall (as part of sessions initiated from behind the DMZ inside router-firewall) through the DMZ outside router-firewall and reach the servers within the DMZ?
1D. What application protocols should be allowed to exit to the Internet (as part of sessions initiated from DMZ servers) through the DMZ outside router-firewall from the servers within the DMZ?
Table 1
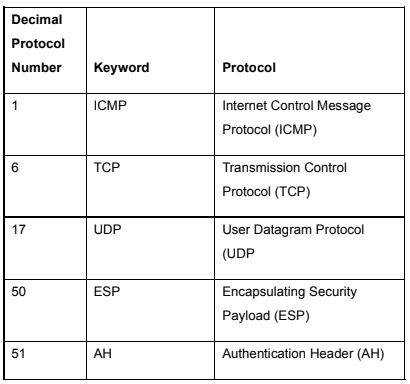
Table 2
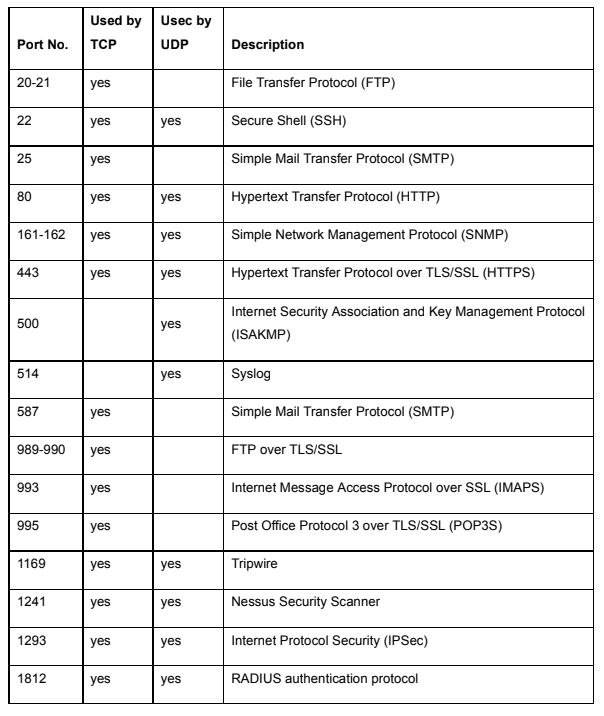
Table 3
Decimal Protocol Number Keyword Protocol ICMP Internet Control Message Protocol (ICMP) Transmission Control Protocol (TCP) User Datagram Protocol (UDP Encapsulating Security Payload (ESP) Authentication Header (AH) TCP 17 UDP 50 ESP 51 AH
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


