Question: ver sequrity.docx D . W cyber sequrity (1).docx + Home Insert Page Layout References Review View Section Tools Q Click Calibri (Body) + 11 At
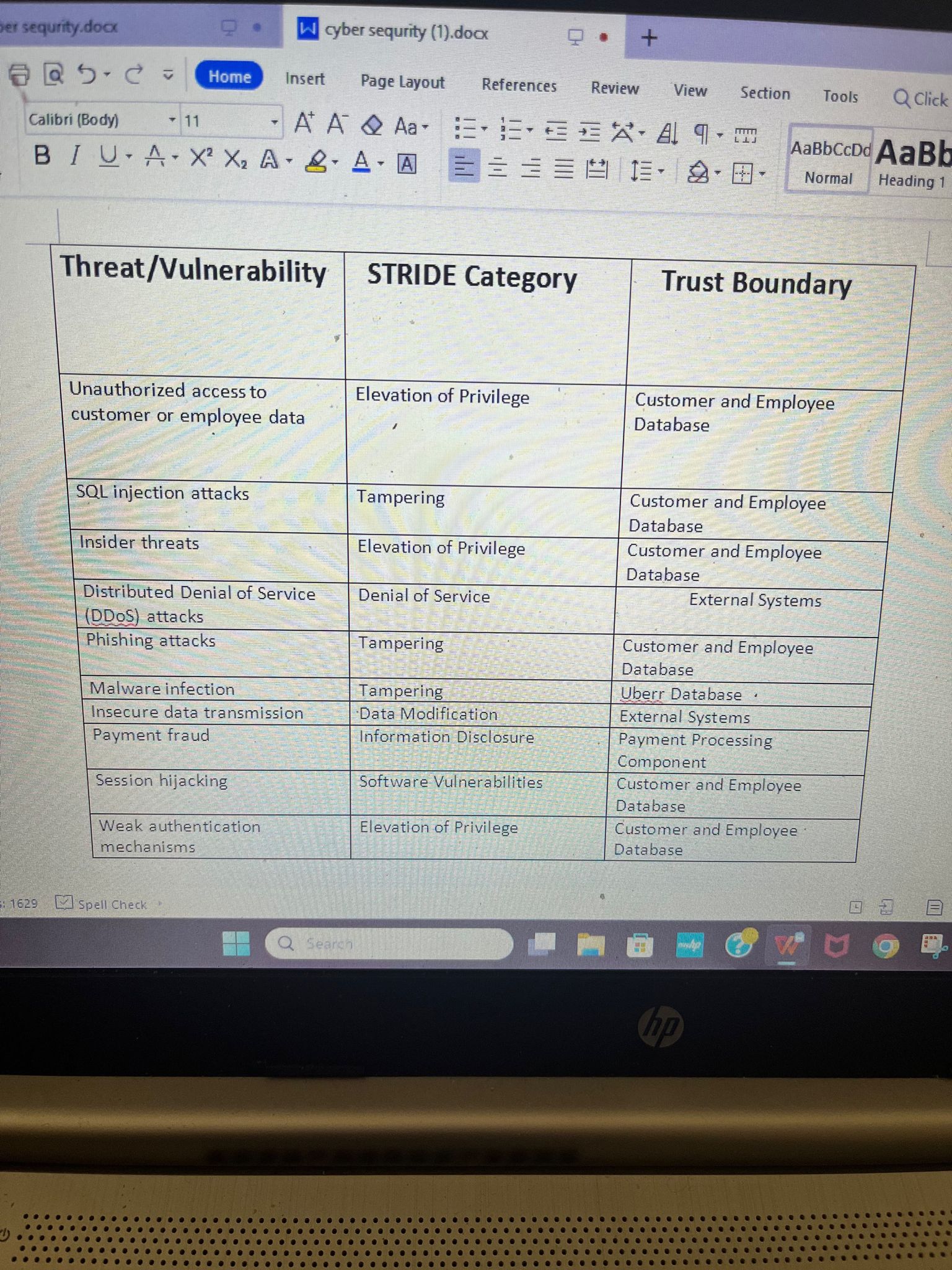

ver sequrity.docx D . W cyber sequrity (1).docx + Home Insert Page Layout References Review View Section Tools Q Click Calibri (Body) + 11 At A & Aa- AaBbCcDd AaBb BI U - A - X' XA . ZAA = =HE- 9.. Normal Heading Threat/Vulnerability STRIDE Category Trust Boundary Unauthorized access to Elevation of Privilege Customer and Employee customer or employee data Database SQL injection attacks Tampering Customer and Employee Database Insider threats Elevation of Privilege Customer and Employee Database Distributed Denial of Service Denial of Service External Systems (DDOS) attacks Phishing attacks Tampering Customer and Employee Database Malware infection Tampering Uberr Database Insecure data transmission Data Modification External Systems Payment fraud Information Disclosure Payment Processing Component Session hijacking Software Vulnerabilities Customer and Employee Database Weak authentication Elevation of Privilege Customer and Employee mechanisms Database 1629 Spell Check Q Search3:06 .1 5G 75 and security to recommend practical solutions towards their resolution. d) Evaluate and communicate relevant technical and ethical 1 of 7 considerations related to the design, deployment and/or the uses of secure technologies within various organisational contexts. Submission For regular class (12 Weeks Duration): By 11:55 pm AEST/AEDT Sunday of Module 4.1 (week 7) For intensive class (6 Weeks Duration): By 11:55 pm AEST/AEDT Sunday of Module 4.2 (week 4) Weighting 30% Total Marks 100 Marks Assessment Task and Context The goal of this assessment is to identify the threats or vulnerabilities in the case scenario described in the associated file, Assessment Initial Case Scenario.docx. NOT all threats or vulnerabilities you "discover" are in the initial case scenario. The scenario discusses some elements of the business that are needing mitigation, but you will need to also "discover" other threats or vulnerabilities. You should use this assessment brief document to guide what to include in this assessment and usethe provided case study to help demonstrate understanding of the topic. Instructions To successfully complete this assessment, your MIS607 Assessment 2 MUST include: Data Flow Diagram (DFD) - The DFD must relate to the business described in the initial case scenario. You must remember that the DFD is the FIRST step in the "Risk Analysis" process, but it is not the main output of this assessment. The main output of MIS607 Assessment 2 is the categorized threats (see below). For the DFD section of your report, you will need to present at least a "Context Diagram" anda "Level-0 Diagram". You can include further levels of DFD (e.g. Level-1, Level-2) if you feel they are needed to show a threat boundary, but it's not necessary. MIS607_Assessment 2 Brief_Threat Model Report Page 1 of 7 TORRENS UNIVERSITY AUSTRALIA The level-0 diagram (and further level diagrams, if needed) must not break the rule for properDFD formation/development. And the DFDs (excluding the Context Diagram) MUST have labelled threat boundaries. You MUST use the below symbol conventions shown and used in classes when developing anddrawing the DFDs: Process Data Flow Data Store Entity " Threats Discovery - The main output of MIS607 Assessment 2 should be a table with a set of minimum 10 throate or vulnerabilities that nood mitigation in the race cranaria -prod-fleet01-xythos.content.blackboardcdn.com4:03 all 5G 61 Safari cdn.fbsbx.com Done MBIS607_Assessment_2_Brief_Case Scenario 2 of 8 TORRENS UNIVERSITY AUSTRALIA dom%20of%20crowds%20management%20discovery&clusterResults=tr ue&stickyFacetsChecked=true&groupVariantRecords=false -000- Uberr Australia Pty Ltd is a company that specialises in local passenger transportation, and local courier services. The company has branches in all major cities in Australia. Recently, the company has suffered a data breach and they are looking to improve their security generally. As an expert cybersecurity consultant, you have been called upon to investigate and improve the security of Uberr. Assume the data leak is exactly the same attack that occurred to Uber in September 2022. You need to research this attack and the details surrounding the attack. Your DFD model should include trust boundaries around the customer and employee data base. Note that the data of employees is just as sensitive as the data of customers. Include other trust boundaries and other possible threats closely following the Uber business model. The threat of data leak is of utmost importance for Uberr, but they are also seeking to tighten overall security. You can assume that ransomware attacks are important, especially those that begin with fishing attacks. You should investigate Uberr (and Uber) and try to find another attack that you think they need to secure against based on your research. (There is a list of possible attacks below, but you can choose another if you wish.) The threat discovery in your report should cover these three threats. You will "discover" other threats (no less than 10 overall) and you can include these in your threat list. Each threat must be mapped against a STRIDE category and associated with a trust boundary from the business model. This should be presented in a clear table that could be easily understood by board and upper management. You have agreed to provide Uberr with two reports. The first report (assessment 2) will list 10 or more threats and outline threat discovery, with a deeper report on discovery for three of the threats. Three of the threats require a few paragraphs explaining discovery techniques as if you performed the discovery personally. MBIS607_Assessment_2_Brief_Case Scenario TORRENS TT UNIVERSITY AUSTRALIA . . . .. ...
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


