Question: Virtual Private Network N 8 . 2 . To l o g into SIUC's network, Bob needs to use a TLS - based VPN .
Virtual Private Network
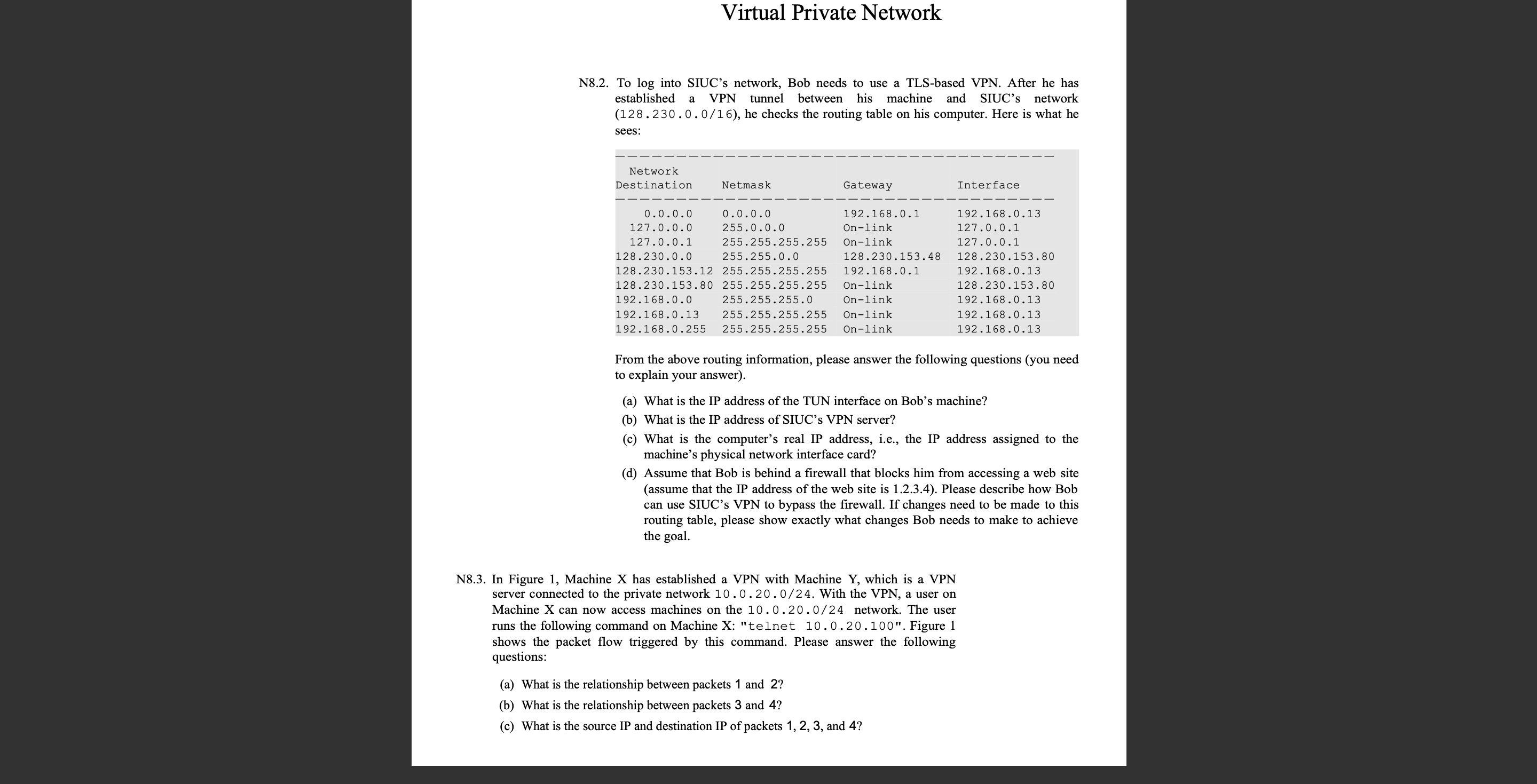
N To into SIUC's network, Bob needs to use a TLSbased VPN After he has
established a VPN tunnel between his machine and SIUC's network
he checks the routing table on his computer. Here is what he
sees:
From the above routing information, please answer the following questions you need
to explain your answer
a What is the IP address of the TUN interface on Bob's machine?
b What is the IP address of SIUC's VPN server?
c What is the computer's real IP address, ie the IP address assigned to the
machine's physical network interface card?
d Assume that Bob is behind a firewall that blocks him from accessing a web site
assume that the IP address of the web site is Please describe how Bob
can use SIUC's VPN to bypass the firewall. If changes need to be made to this
routing table, please show exactly what changes Bob needs to make to achieve
the goal.
N In Figure Machine has established a VPN with Machine which is a VPN
server connected to the private network With the VPN a user on
Machine X can now access machines on the network. The user
runs the following command on Machine X: "telnet Figure
shows the packet flow triggered by this command. Please answer the following
questions:
a What is the relationship between packets and
b What is the relationship between packets and
c What is the source IP and destination IP of packets and
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


