Question: We Discussed about using 4 bytes state and 2 bytes key for stream generation. Assuming that K = [2,1] and the permutation S = [1,2,3,0]
We Discussed about using 4 bytes state and 2 bytes key for stream generation. Assuming that K = [2,1] and the permutation S = [1,2,3,0] has been obtained after Step 2 (initial permutation of S). Write a Program to complete the followings:
1. Complete the Stream generation step (step 3) to obtain streams.
2. USing the streams to encrypt the message: "HI" (H = 01001000 and I = 01001001)
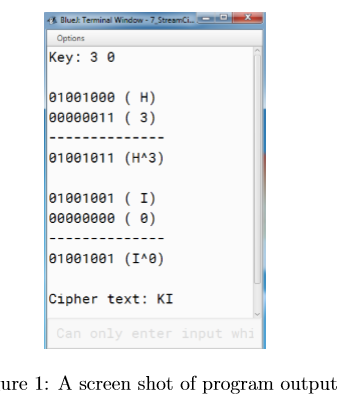
Your output should look like the following screenshot.
 public class StreamCipher { public static String encryption (char p, int k) {
public class StreamCipher { public static String encryption (char p, int k) {
String res="";
// xor int c = p ^ k;
// Binary representation String b4p = String.format("%8s", Integer.toBinaryString((int)p)).replace(' ', '0'); String b4k = String.format("%8s", Integer.toBinaryString(k)).replace(' ', '0'); String b4c = String.format("%8s", Integer.toBinaryString(c)).replace(' ', '0');
// print out System.out.printf("%s (%2c) ", b4p,p); System.out.printf("%s (%2d) ", b4k, k); System.out.printf("-------------- "); System.out.printf("%s (%c^%d) ", b4c, p,k);
// print out the corresponding letter res += (char) c;
return res; }
public static int [] streamGeneration (int keylen) { int key [] = new int[keylen]; int S[] = {1,2,3,0};
int i = 0; int j = 0; int count = 0; int temp, t;
// ......
return key; }
public static void main () {
// key generation int [] key = streamGeneration (2);
System.out.print("Key: "); for (int k=0; k System.out.print(key[k] + " "); } System.out.println(" ");
// encryption String cipher = encryption ('A', 3); System.out.printf("Cipher text: %s ", cipher);
} }
Options Key: 3 91881008 (H) 00000011 (3) 91001811 (HA3) 91001001 I) eee00eee ) 91881881 (IAB) Cipher text: KI an only enter input whi ure 1: A screen shot of program output
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


