Question: We have learned that private keys should never be reused when encrypting messages using the one-time pad cipher/algorithm. In this problem, we establish this fact
We have learned that private keys should never be reused when encrypting messages using the one-time pad cipher/algorithm. In this problem, we establish this fact through an attack. In particular, we find how we can retrieve the encryption key k given two ciphertexts encrypted with that same key along with some auxiliary information about the messages.
Each student is provided with two distinct ciphertexts c1 and c2 encrypted with the distinct key ksuch that
c1 = m1 k
c2 = m2 k
Here, m1 and m2 are two messages. The auxiliary information about the messages m1 and m2 is that they are very prominent school's slogans.
Tasks:
Determine the messages m1 and m2, along with the encryption key k and report them in your solution in the ASCII character format as a string.
Each student is also provided with another distinct ciphertext c3 which encrypts an unknown message m3 with the same key k (as in c1 and c2). The second task is to retrieve message m3 and report it in your assignment solution in the ASCII character format as a string.
Remarks:
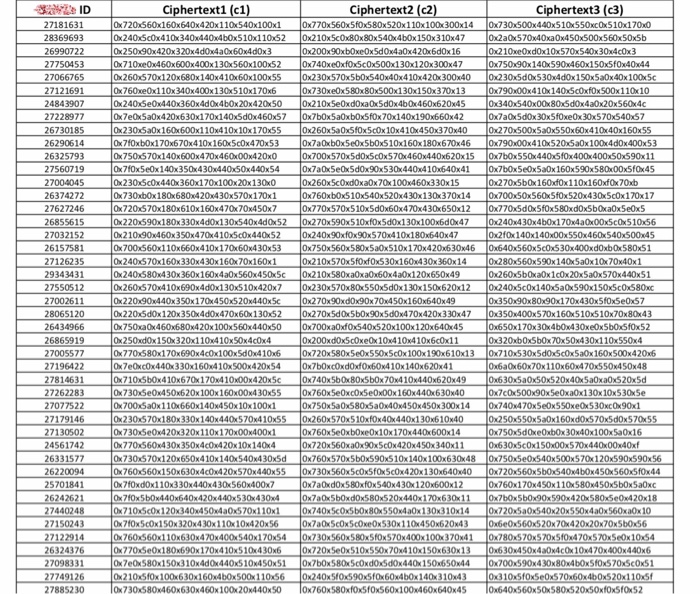
Each student is only supposed to attack a set of ciphertexts c1,c2,c3 indexed by his/her IDs in Figure 1.
In Figure 1, all ciphertexts are written in hex format. For example character a is represented as0x61 which has decimal ASCII value of 97.
The XORing procedure in the one-time pad algorithm is performed at the bit level. For example, to XOR 0x76 and 0x42, we first represent them in the binary format and then perform bitwise XOR; i.e.,
0x76 = 01110110
0x42 = 00100010 0x76 0x42 = 01010100 = 0x34
For every student, message m3 is a meaningful, distinct word. Thus, if you compute a message that does not make sense try again.
If you perform computation over a paper (by hand), write down step-by-step solutions for both tasks and not just the end results. If you write small programs to solve the problem instead, please include the snippet of your code in the pdf file.
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


