Question: What did the attacker use to exploit the e - commerce web application vulnerability? Web server logs Forced browsing User error Data breach What recommendations
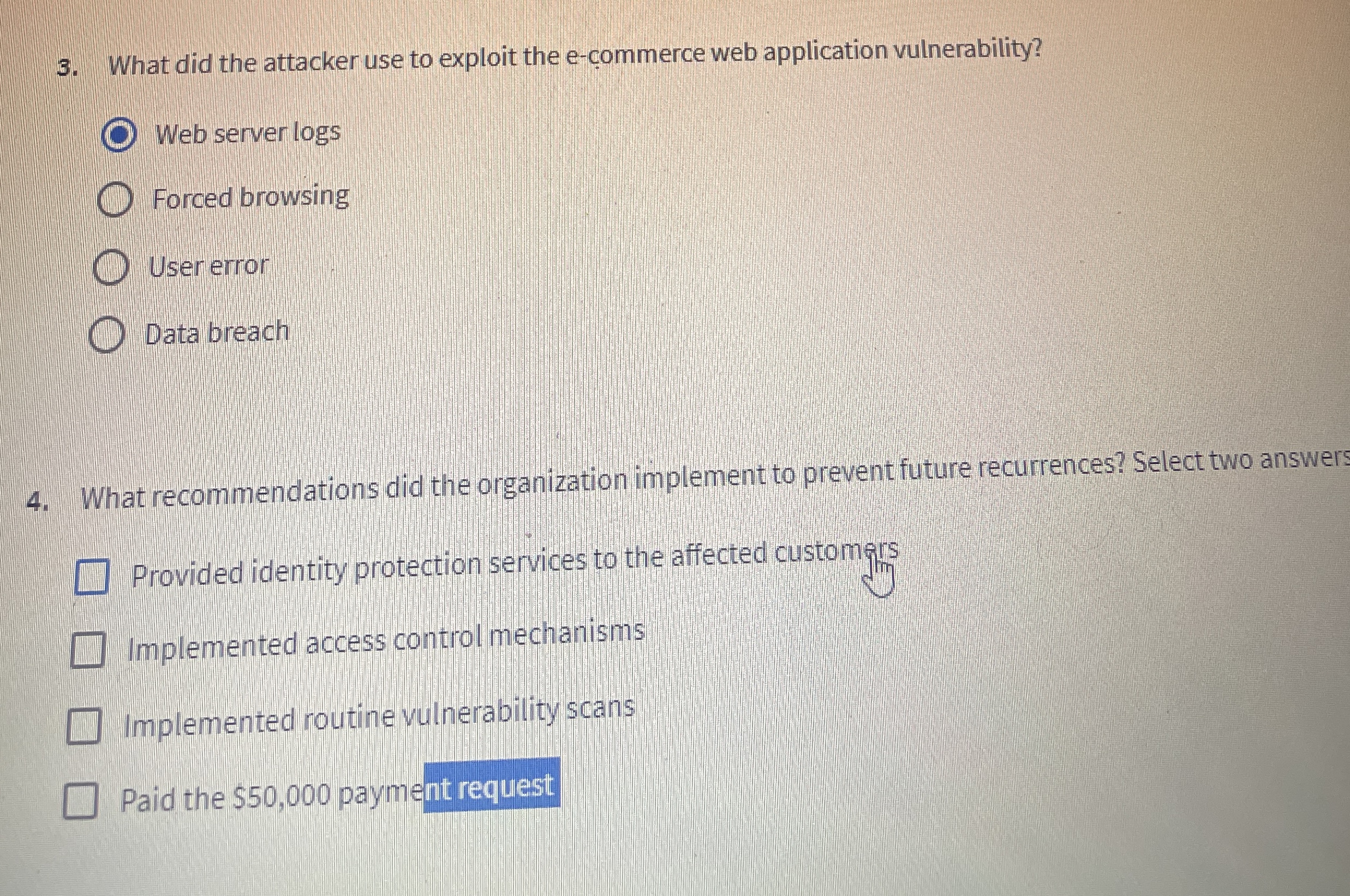
What did the attacker use to exploit the ecommerce web application vulnerability?
Web server logs
Forced browsing
User error
Data breach
What recommendations did the organization implement to prevent future recurrences? Select two answers
Provided identity protection services to the affected customers
Implemented access control mechanisms
Implemented routine vulnerability scans
Paid the $ payment request
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


