Question: What does it require to make SQL injection attack successful? Understanding web programming Creating a SQL statement that force one to input correct password Creating
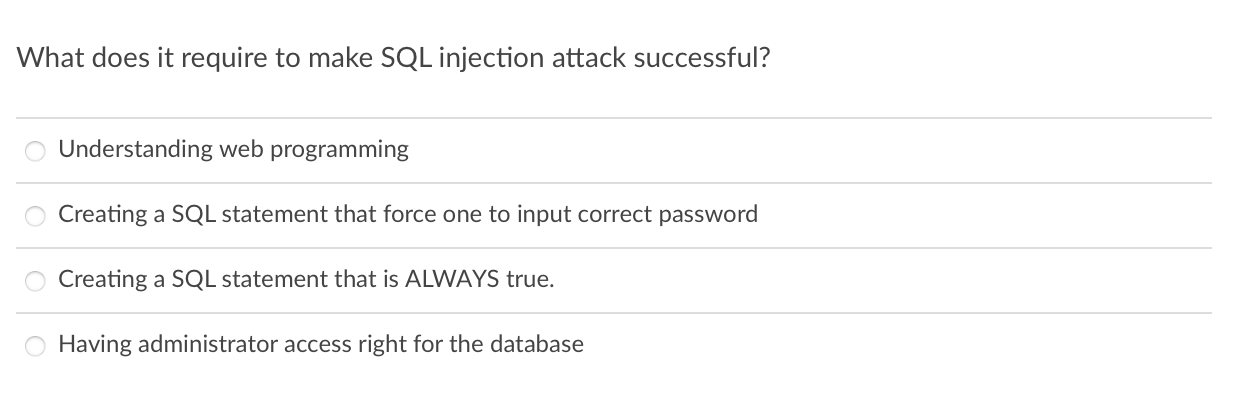

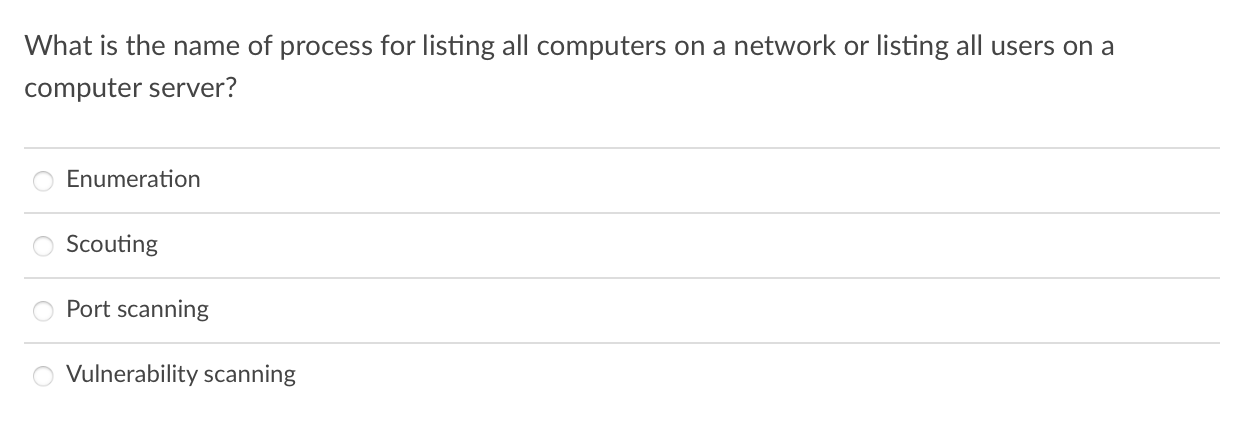
What does it require to make SQL injection attack successful? Understanding web programming Creating a SQL statement that force one to input correct password Creating a SQL statement that is ALWAYS true. Having administrator access right for the database What is the most effective way to prevent SQL injection attack and cross site scripting attack? Use the firewall They can not be prevented Use an IDS Filter the input What is the name of process for listing all computers on a network or listing all users on a computer server? Enumeration Scouting Port scanning Vulnerability scanning
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


