Question: What is the most appropriate response strategy for mitigating the risk of a cyber - attack on a company's network infrastructure using the Analytical Hierarchy
What is the most appropriate response strategy for mitigating the risk of a cyberattack on a company's network infrastructure using the Analytical Hierarchy Process AHP approach? The type of risk, along with its potential response strategies, are outlined below:
Maninthemiddle attacks: In this type of attack, a cybercriminal intercepts communication between two parties to steal sensitive data or manipulate the conversation.
Response Strategies:
Response : Implementing network segmentation and access controls. This strategy involves dividing the company's network into smaller, more secure segments, each with its own access controls. This limits the damage that a cyber attacker can do if they gain access to the network. By implementing access controls, the organisation can restrict access to specific areas of the network based on the user's role or clearance level.
Response : Conducting regular vulnerability assessments and penetration testing. Regular vulnerability assessments and penetration testing can help identify vulnerabilities and weaknesses in the organisation's network infrastructure. These assessments can be used to prioritise security efforts and address vulnerabilities before they can be exploited by attackers.
Response : Deploying intrusion detection and prevention systems. Intrusion detection and prevention systems are designed to detect and block malicious traffic in realtime. These systems can be used to monitor network traffic, identify suspicious activity, and prevent attacks from gaining a foothold on the network.
Response : Implementing employee security awareness training and policies. Employees can be a significant vulnerability in a company's cybersecurity efforts. Implementing regular security awareness training and policies can help ensure that employees are aware of the risks associated with cybersecurity and the steps they can take to protect the organisation's network and data.
Response : Regularly backing up critical data and implementing disaster recovery plans. Regular data backups and disaster recovery plans can help ensure that the organisation can quickly recover from a cyberattack or other disaster. By regularly backing up data and implementing disaster recovery plans, the organisation can minimise the impact of an attack and quickly resume normal operations.
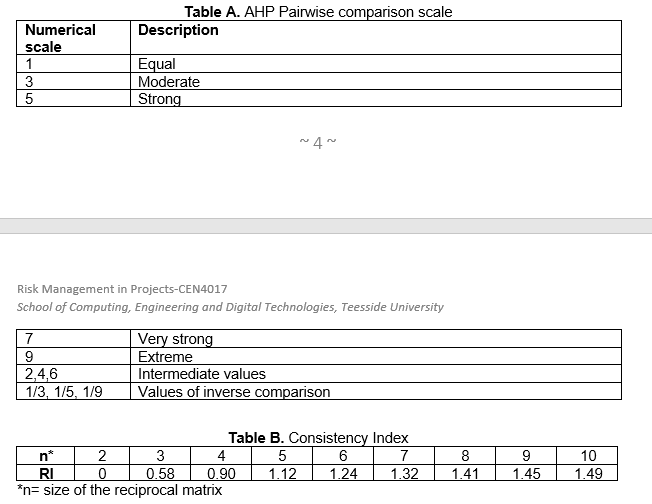
Considering the resources available within your organisation, including the availability of expertise in risk management and contingencies for risk management activities, as well as the support of upper management, please develop at least four selection criteria for the risk response strategies. Please refer to Table A to derive the AHP pairwise comparison scales and to Table B for consistency index.
Conclude your analysis with a brief discussion on the efficacy of the approach
size of the reciprocal matrix
Very important to provide references
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


