Question: What type of programming error is an attacker likely to attempt to exploit? Runtime Compile-time Differentiation Structured exception handling Which part of the CIA triad
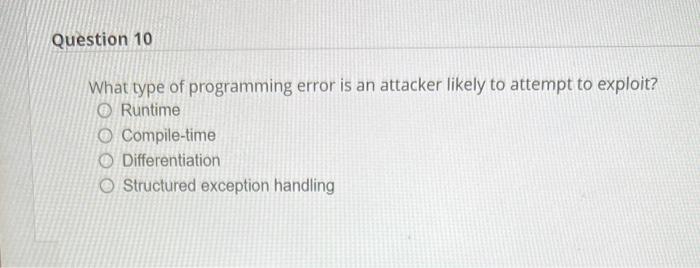
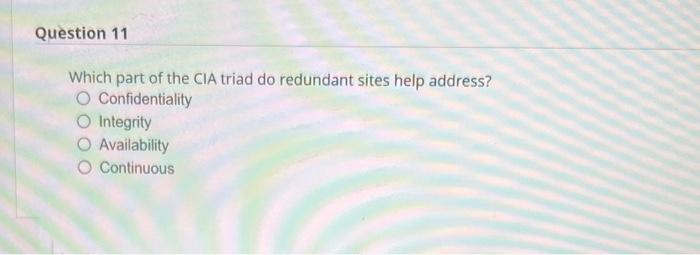
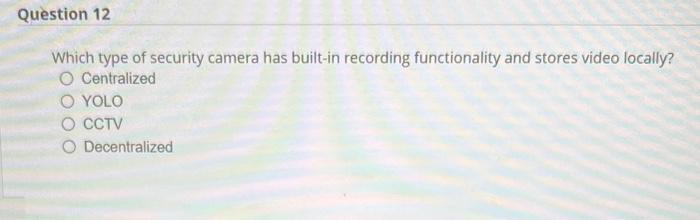
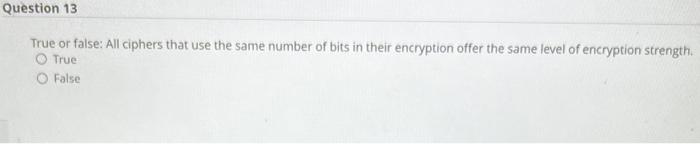

What type of programming error is an attacker likely to attempt to exploit? Runtime Compile-time Differentiation Structured exception handling Which part of the CIA triad do redundant sites help address? Confidentiality Integrity Availability Continuous Which type of security camera has built-in recording functionality and stores video locally? Centralized YOLO CCTV Decentralized True or false: All ciphers that use the same number of bits in their encryption offer the same level of encryption strength. True False Substitution and tokenization are techniques for doing what? Data masking Decryption Password discovery Rights management In the software development life cycle (SDLC), which of these comes after the Deployment phase? Design Implementation Maintenance Integration Raspberry Pi and Arduino boards are examples of what? Embedded system Industrial control system loT device SoC
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


