Question: Whats wrong with the protocol in Authentication ? (Hint: assume Alice can open two connections to Bob.) Alice Bob -A encrypted with KAB B 'B
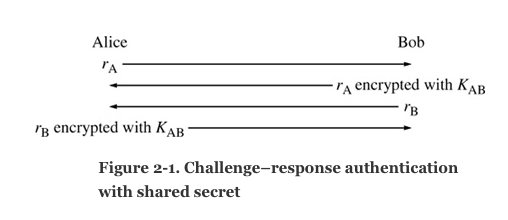
Whats wrong with the protocol in Authentication? (Hint: assume Alice can open two connections to Bob.)
Alice Bob -A encrypted with KAB "B 'B encrypted with KAB- Figure 2-1. Challenge-response authentication with shared secret
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


