Question: Which example below best describes an insider attack? Which example below best describes an insider attack? doing a power analysis attack on a stolen smart
Which example below best describes an insider attack?
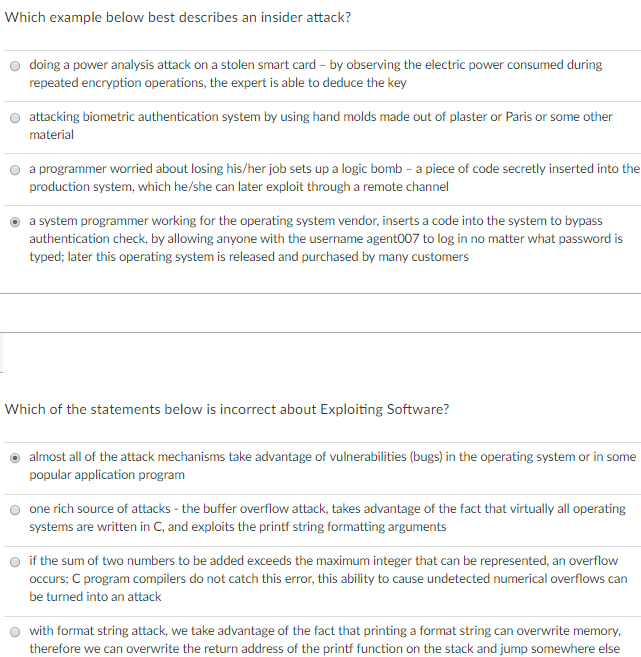
Which example below best describes an insider attack? doing a power analysis attack on a stolen smart card-by observing the electric power consumed during repeated encryption operations, the expert is able to deduce the key O attacking biometric authentication system by using hand molds made out of plaster or Paris or some other material O a programmer worried about losing his/her job sets up a logic bomb - a piece of code secretly inserted into the production system, which he/she can later exploit through a remote channel O a system programmer working for the operating system vendor, inserts a code into the system to bypass authentication check, by allowing anyone with the username agent007 to log in no matter what password is typed; later this operating system is released and purchased by many customers o Which of the statements below is incorrect about Exploiting Software? almost all of the attack mechanisms take advantage of vulnerabilities (bugs) in the operating system or in some opular application program one rich source of attacks - the buffer overflow attack, takes advantage of the fact that virtually all operating systems are written in C, and exploits the printf string formatting arguments O occurs; C program compilers do not catch this error, this ability to cause undetected numerical overflows can be turned into an attack with format string attack, we take advantage of the fact that printing a format string can overwrite memory, therefore we can overwrite the return address of the printf function on the stack and jump somewhere else o
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


