Question: While investigating suspicious activity on a server, a security administrator runs the following report File system integrity check report Total number of files: 3321 Added
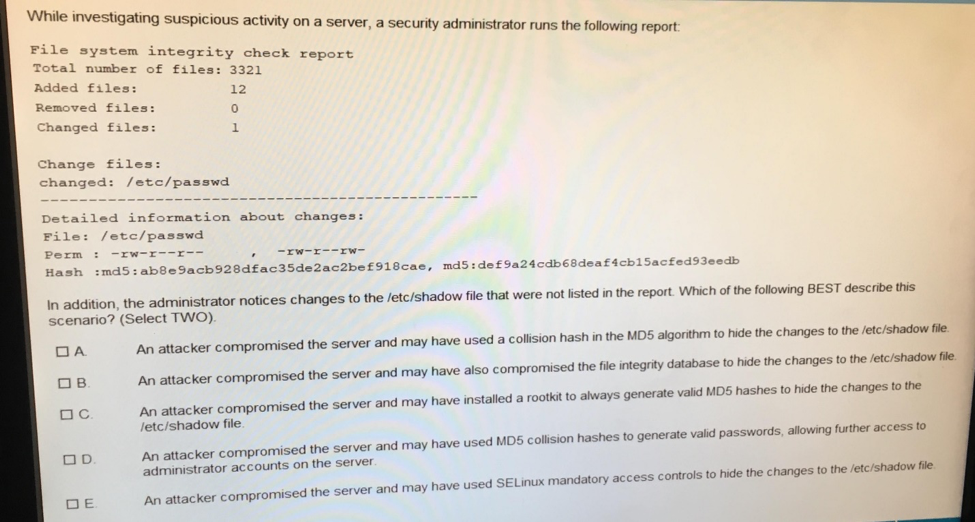
While investigating suspicious activity on a server, a security administrator runs the following report File system integrity check report Total number of files: 3321 Added files: Removed files: Changed files: 12 0 1 Change files: changed: /etc/passwd Detailed information about changes: File: /etc/passwd -rw-r-rw fac35de 2 ac2be f 9 1 8 cae, md5 : de f9a24cdb68deaf4cb15acfed93eedb Hash :md5 : ab8e9acb928d rator notices changes to the letc/shadow file that were not listed in the report. Which of the scenario? (Select TWO) An attacker compromised the server and may have used a collision hash in the MD5 algorithm to hide the changes to the /etc/shadow file An attacker compromised the server and may have also compromised the file integrity database to hide the changes to the /etc/shadow file An attacker compromised the server and may have installed a rootkit to always generate valid MD5 hashes to hide the changes to the etc/shadow file C. An attacker compromised the server and may have used MD5 collision hashes to generate valid passwords, allowing further access to administrator accounts on the server D. An attacker compromised the server and may have used SELinux mandatory access controls to hide the changes to the /etc/shadow file
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


