Question: With reference to the construction of HMAC, explain how changing the design of the API in Part 1.2 to use token = HMAC_user's password(user =
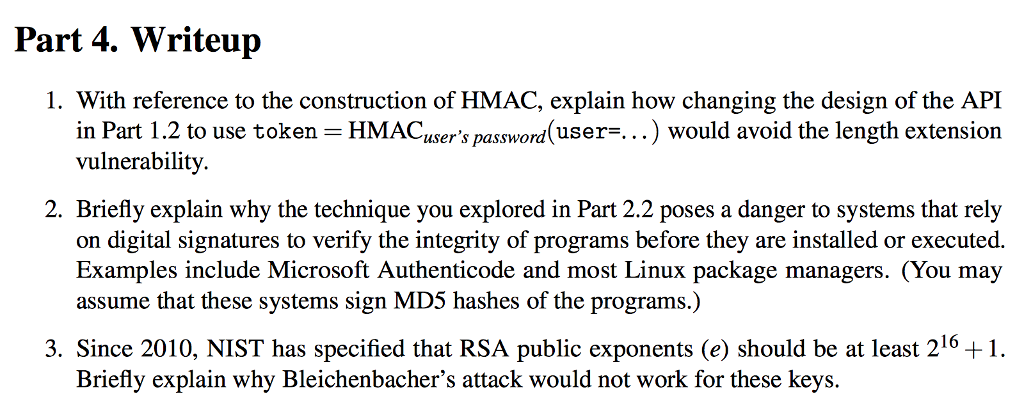
With reference to the construction of HMAC, explain how changing the design of the API in Part 1.2 to use token = HMAC_user's password(user = ...) would avoid the length extension vulnerability Briefly explain why the technique you explored in Part 2.2 poses a danger to systems that rely on digital signatures to verify the integrity of programs before they are installed or executed. Examples include Microsoft Authenticode and most Linux package managers. (You may assume that these systems sign MD5 hashes of the programs.) Since 2010, NIST has specified that RSA public exponents (e) should be at least 2^16 +1. Briefly explain why Bleichenbacher's attack would not work for these keys. With reference to the construction of HMAC, explain how changing the design of the API in Part 1.2 to use token = HMAC_user's password(user = ...) would avoid the length extension vulnerability Briefly explain why the technique you explored in Part 2.2 poses a danger to systems that rely on digital signatures to verify the integrity of programs before they are installed or executed. Examples include Microsoft Authenticode and most Linux package managers. (You may assume that these systems sign MD5 hashes of the programs.) Since 2010, NIST has specified that RSA public exponents (e) should be at least 2^16 +1. Briefly explain why Bleichenbacher's attack would not work for these keys
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


