Question: Write a program using only the following MIPS instructions: The memory reference instructions load word (lw) and store word (sw) The arithmetic-logical instructions add,
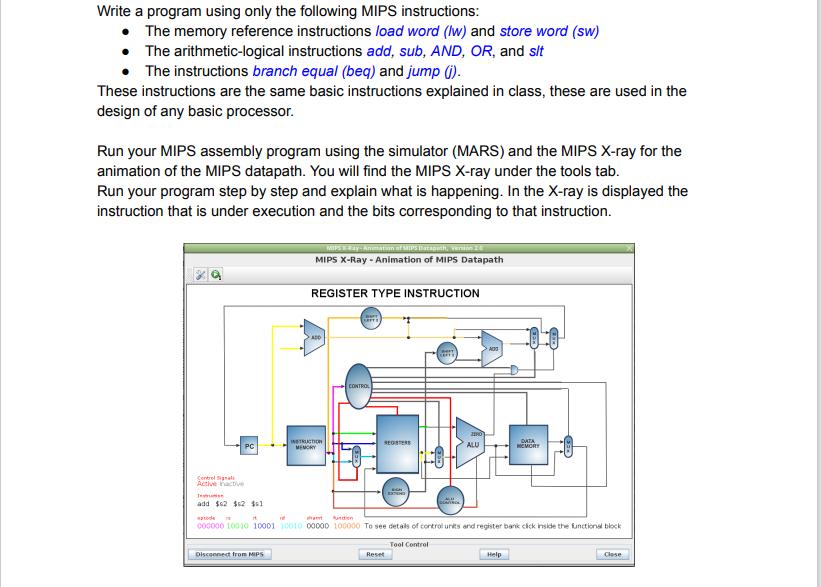
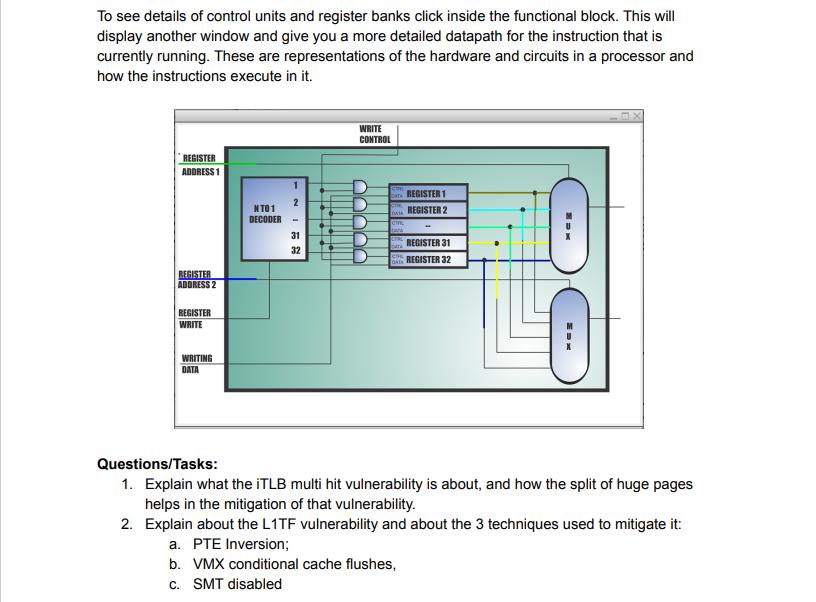
Write a program using only the following MIPS instructions: The memory reference instructions load word (lw) and store word (sw) The arithmetic-logical instructions add, sub, AND, OR, and sit The instructions branch equal (beq) and jump (j). These instructions are the same basic instructions explained in class, these are used in the design of any basic processor. Run your MIPS assembly program using the simulator (MARS) and the MIPS X-ray for the animation of the MIPS datapath. You will find the MIPS X-ray under the tools tab. Run your program step by step and explain what is happening. In the X-ray is displayed the instruction that is under execution and the bits corresponding to that instruction. PC Control Signals Active active Jesse add $62 $2 $1 MIPS Ray-Animation of SHIPS Datapeth, version 2.0 MIPS X-Ray - Animation of MIPS Datapath Disconnect from MIPS REGISTER TYPE INSTRUCTION ADD INSTRUCTION MEMORY CONTROL REGSTERS CH EXTING Reset DEAVTROK Tool Control 1180 ALU pode in ht funcion 000000 10010 10001 10010 00000 100000 To see details of control units and register bank cick inside the functional block A00 DATA HOVORY Help Close To see details of control units and register banks click inside the functional block. This will display another window and give you a more detailed datapath for the instruction that is currently running. These are representations of the hardware and circuits in a processor and how the instructions execute in it. REGISTER ADDRESS 1 REGISTER ADDRESS 2 REGISTER WRITE WRITING DATA NT01 DECODER 1 2 - 31 32 6 WRITE CONTROL cm. LUL REGISTER 1 REGISTER 2 REGISTER 31 REGISTER 32 Questions/Tasks: 1. Explain what the iTLB multi hit vulnerability is about, and how the split of huge pages helps in the mitigation of that vulnerability. 2. Explain about the L1TF vulnerability and about the 3 techniques used to mitigate it: a. PTE Inversion; b. VMX conditional cache flushes, c. SMT disabled
Step by Step Solution
3.51 Rating (151 Votes )
There are 3 Steps involved in it
An example program using the MIPS instructions you have listed data array word 1 2 3 4 5 Initialize ... View full answer

Get step-by-step solutions from verified subject matter experts


