Question: Write this python program in Unix Netcat (NC) is a wonderful little program that system security analysts hate. You're going Write a single program, in
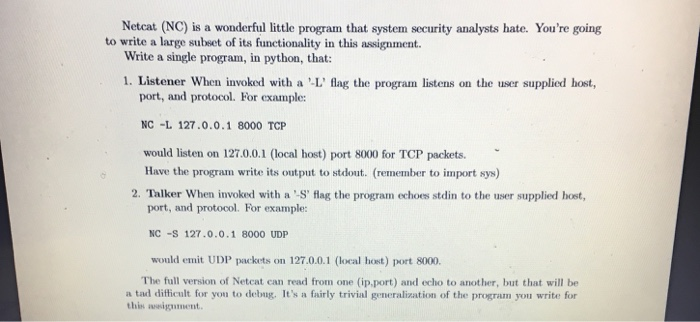
Netcat (NC) is a wonderful little program that system security analysts hate. You're going Write a single program, in python, that: 1. Listener When invoked with a 'L' flag the program listens on the user supplied host, to write a large subset of its functionality in this assignment port, and protocol. For example NC -L 127.0.0.1 8000 TCP would listen on 127.0.0.1 (local host) port 8000 for TCP packets. Have the program write its output to stdout. (remember to import sys) 2. Talker When invoked with a 'S' flag the program echoes stdin to the user supplied host, port, and protocol. For example: NC -S 127.0.0.1 8000 UDP would emit UDP packets on 127.0.0.1 (local host) port 8000. The full version of Netcat can read from one (ip.port) and echo to another, but that will be a tad difficult for you to debug. It's a fairly trivial generalization of the program you write for thin ansigmment. Netcat (NC) is a wonderful little program that system security analysts hate. You're going Write a single program, in python, that: 1. Listener When invoked with a 'L' flag the program listens on the user supplied host, to write a large subset of its functionality in this assignment port, and protocol. For example NC -L 127.0.0.1 8000 TCP would listen on 127.0.0.1 (local host) port 8000 for TCP packets. Have the program write its output to stdout. (remember to import sys) 2. Talker When invoked with a 'S' flag the program echoes stdin to the user supplied host, port, and protocol. For example: NC -S 127.0.0.1 8000 UDP would emit UDP packets on 127.0.0.1 (local host) port 8000. The full version of Netcat can read from one (ip.port) and echo to another, but that will be a tad difficult for you to debug. It's a fairly trivial generalization of the program you write for thin ansigmment
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


