Question: Writing ACLs for given network with the given specifications Exercise 1: This assignment consists of just one exercise on access control lists (ACL). Study the
Writing ACLs for given network with the given specifications
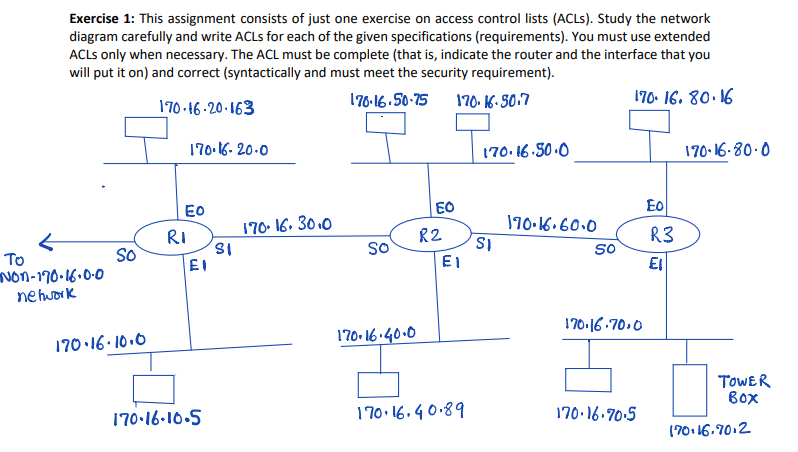
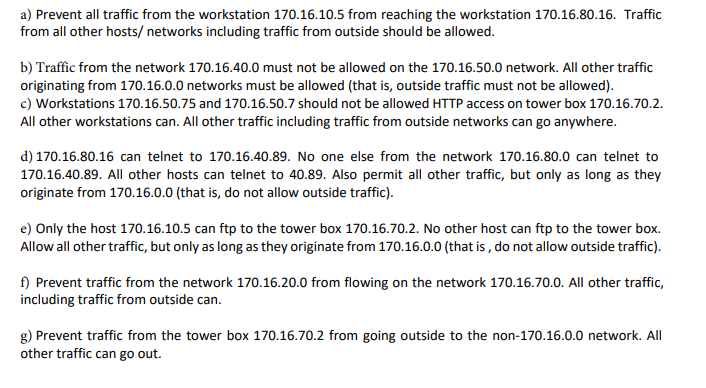
Exercise 1: This assignment consists of just one exercise on access control lists (ACL). Study the network diagram carefully and write ACLs for each of the given specifications (requirements). You must use extended ACLs only when necessary. The ACL must be complete (that is, indicate the router and the interface that you will put it on) and correct (syntactically and must meet the security requirement). 176.16.50-75 170.16-20.163 170 16.80.16 170.16.50.7 170.16-20.0 170.16-50.0 170-16-80.0 ED EO so R2 190.16.60.0 ( R3 SO SR TE, S10-16.30,0 Non-170.16.0.0 nehwork 170.16.70.0 170.16.40.0 170.16.10.0 TOWER BOX 170-16-10-5 170.16.40.89 170.16.70.5 17016.70.2 a) Prevent all traffic from the workstation 170.16.10.5 from reaching the workstation 170.16.80.16. Traffic from all other hosts/ networks including traffic from outside should be allowed. b) Traffic from the network 170.16.40.0 must not be allowed on the 170.16.50.0 network. All other traffic originating from 170.16.0.0 networks must be allowed (that is, outside traffic must not be allowed). c) Workstations 170.16.50.75 and 170.16.50.7 should not be allowed HTTP access on tower box 170.16.70.2. All other workstations can. All other traffic including traffic from outside networks can go anywhere. d) 170.16.80.16 can telnet to 170.16.40.89. No one else from the network 170.16.80.0 can telnet to 170.16.40.89. All other hosts can telnet to 40.89. Also permit all other traffic, but only as long as they originate from 170.16.0.0 (that is, do not allow outside traffic). e) Only the host 170.16.10.5 can ftp to the tower box 170.16.70.2. No other host can ftp to the tower box. Allow all other traffic, but only as long as they originate from 170.16.0.0 (that is, do not allow outside traffic). f) Prevent traffic from the network 170.16.20.0 from flowing on the network 170.16.70.0. All other traffic, including traffic from outside can. g) Prevent traffic from the tower box 170.16.70.2 from going outside to the non-170.16.0.0 network. All other traffic can go out. Exercise 1: This assignment consists of just one exercise on access control lists (ACL). Study the network diagram carefully and write ACLs for each of the given specifications (requirements). You must use extended ACLs only when necessary. The ACL must be complete (that is, indicate the router and the interface that you will put it on) and correct (syntactically and must meet the security requirement). 176.16.50-75 170.16-20.163 170 16.80.16 170.16.50.7 170.16-20.0 170.16-50.0 170-16-80.0 ED EO so R2 190.16.60.0 ( R3 SO SR TE, S10-16.30,0 Non-170.16.0.0 nehwork 170.16.70.0 170.16.40.0 170.16.10.0 TOWER BOX 170-16-10-5 170.16.40.89 170.16.70.5 17016.70.2 a) Prevent all traffic from the workstation 170.16.10.5 from reaching the workstation 170.16.80.16. Traffic from all other hosts/ networks including traffic from outside should be allowed. b) Traffic from the network 170.16.40.0 must not be allowed on the 170.16.50.0 network. All other traffic originating from 170.16.0.0 networks must be allowed (that is, outside traffic must not be allowed). c) Workstations 170.16.50.75 and 170.16.50.7 should not be allowed HTTP access on tower box 170.16.70.2. All other workstations can. All other traffic including traffic from outside networks can go anywhere. d) 170.16.80.16 can telnet to 170.16.40.89. No one else from the network 170.16.80.0 can telnet to 170.16.40.89. All other hosts can telnet to 40.89. Also permit all other traffic, but only as long as they originate from 170.16.0.0 (that is, do not allow outside traffic). e) Only the host 170.16.10.5 can ftp to the tower box 170.16.70.2. No other host can ftp to the tower box. Allow all other traffic, but only as long as they originate from 170.16.0.0 (that is, do not allow outside traffic). f) Prevent traffic from the network 170.16.20.0 from flowing on the network 170.16.70.0. All other traffic, including traffic from outside can. g) Prevent traffic from the tower box 170.16.70.2 from going outside to the non-170.16.0.0 network. All other traffic can go out
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


