Question: Writing an encryption/decryption method in Java, Please help! Introduction: We will simulate that you are trying to hide some secret information from the rival companies.


Writing an encryption/decryption method in Java, Please help!
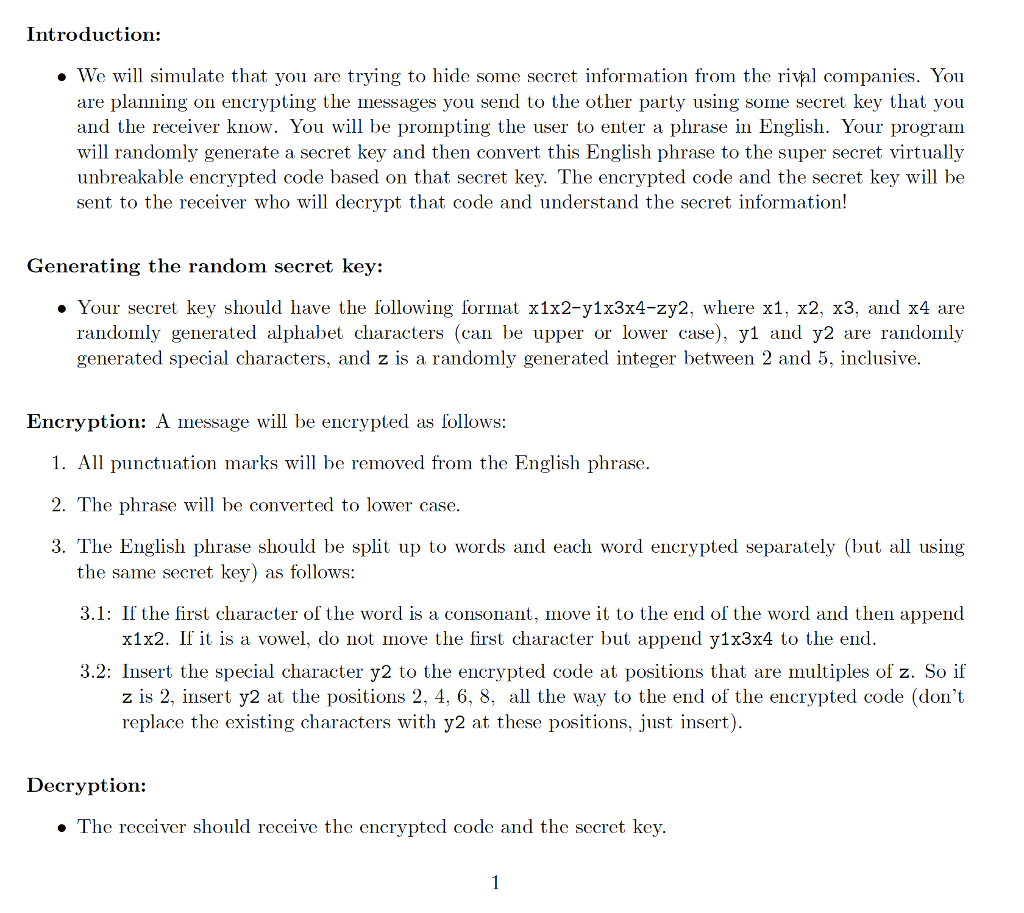
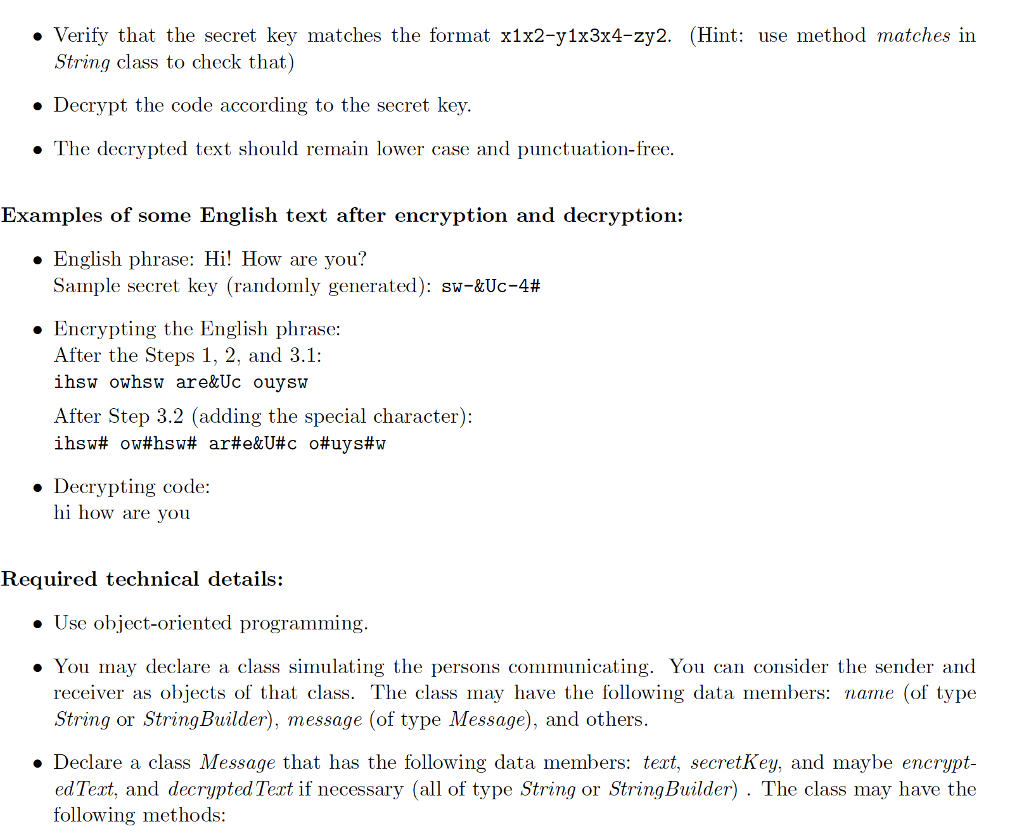
Introduction: We will simulate that you are trying to hide some secret information from the rival companies. You are planning on encrypting the messages you send to the other party using some secret key that you and the receiver know. You will be prompting the user to enter a phrase in English. Your program will randomly generate a secret key and then convert this English phrase to the super secret virtually unbreakable encrypted code based on that secret key. The encrypted code and the secret key will be sent to the receiver who will decrypt that code and understand the secret information! Generating the random secret key: Your secret key should have the following format X1X 1x3x4-zy 2, where x1, x2, x3, and x4 are randomly generated alphabet characters can be upper or lower case 1 and y2 are randomly generated special characters, and z is a randomly generated integer between 2 and 5, inclusive. Encryption: A message will be encrypted as follows: 1. All punctuation marks will be removed from the English phrase 2. The phrase will be converted to lower case 3. The English phrase should be split up to words and each word encrypted separately (but all using the same secret key as follows: 3.1: If the first character of the word is a consonant, move it to the end of the word and then append x1x2. If it is a vowel, do not move the first character but append y1x3x4 to the end 3.2: Insert the special character y2 to the encrypted code at positions that are multiples of z. So if z is 2, insert y2 at the positions 2, 4, 6, 8, all the way to the end of the encrypted code (don't replace the existing characters with y2 at these positions, just insert) Decryption: The receiver should receive the encrypted code and the secret key
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


