Question: Wuch attack type violates the integrity of a database by changing existing data? Modification Interruption Fabncation Intercepton Which security principle is addressed by redundancy? Possession


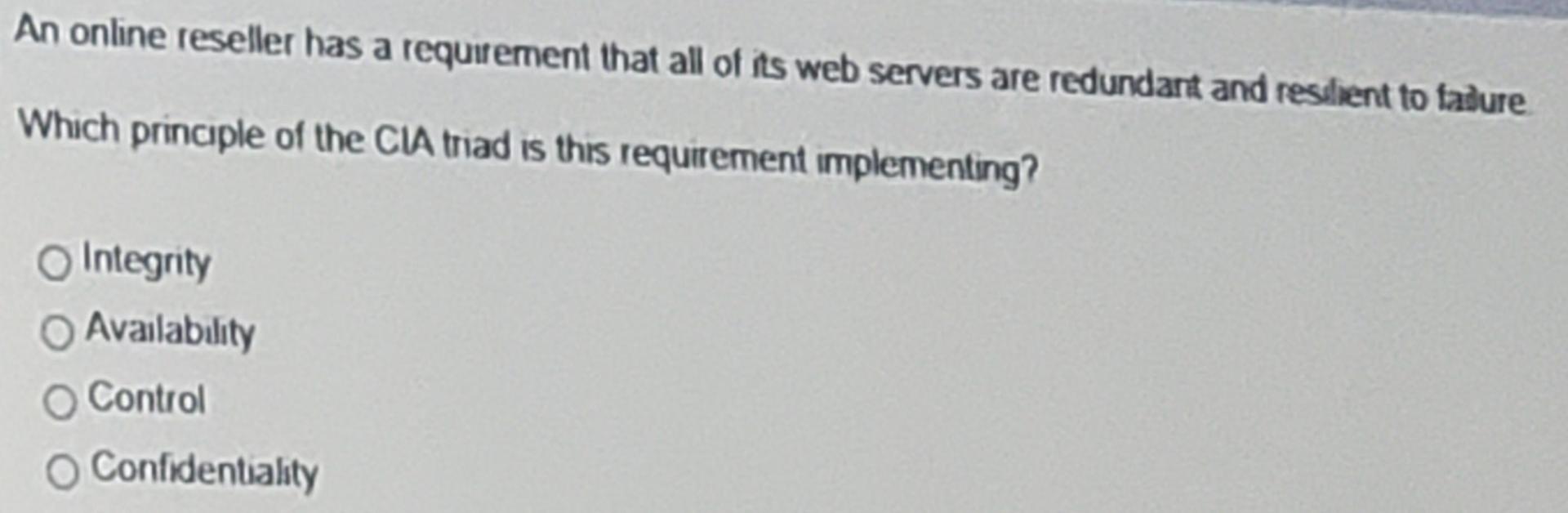
Wuch attack type violates the integrity of a database by changing existing data? Modification Interruption Fabncation Intercepton Which security principle is addressed by redundancy? Possession Integnity Confidentiality Availability An online reseller has a requirement that all of its web servers are redundant and resilient to tadure Which principle of the CIA triad is this requirement implementing? Integrity Availability o Control Confidentialty
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


