Question: Your final major program for CSII will be to creste a pair of command-line programs to compress and decompress arbitrary tiles. This will require some


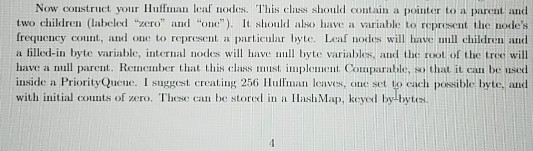
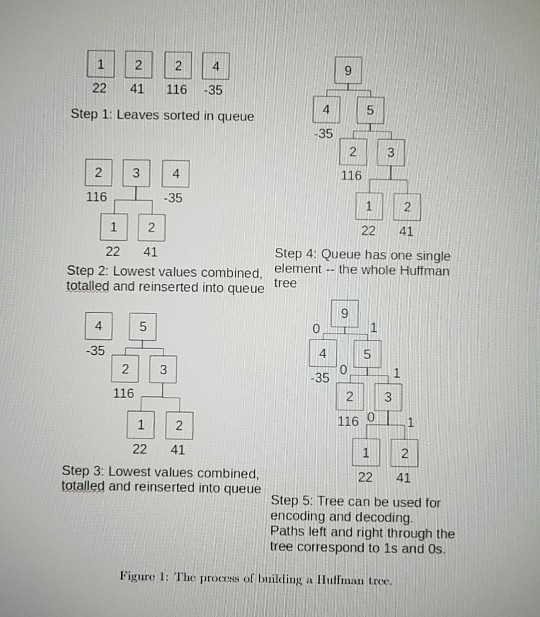
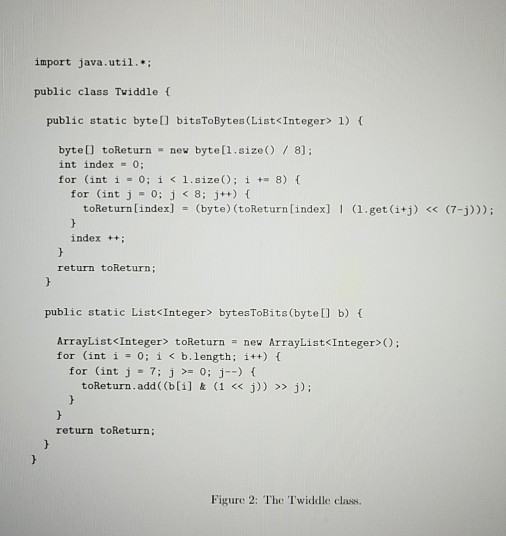

Your final major program for CSII will be to creste a pair of command-line programs to compress and decompress arbitrary tiles. This will require some bit-level operations, creating a Comparable binary tree class that will be used to create bit encodings, and using various Collections classes for counting, sorting and mapping luffiman codes have been around since the carly fiftics, and are still n Modern compression methods use Hulnan codes as part of t r compression techniques on top. Huflman codes are gencral-purpose they can be used to compress any arbitrary byte stream- though they are generally less ellicient then special-purpe that apply only to specific kinds of data. used for data compression he algorithm, and then layer othe The basic idea behind Hufman codes is to represent bytes as variable length bit strings, rather than having every byte be represented by ciglit bits. If commonly-occurring bytes roquire only two or three bits instead of eight, while very uncommon bytes are represented with ten or fifteen, it adds up to a win in file siz Coding and decoding Huffman codes is based on building a binary tree structure known as a Huffman tree. The leaves of the tree represent the bytes of the original tile. The path through a tree from leaf to root (for eneoding) or from root to leaf or deecling) vields a sequence of bits that code for that particular byte. The tree is built in such a way that common bytes are located near the root, while rare ones are located far down the tree. The casicst way to illustrate the process is with an example
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


