Question: Your team is tasked with developing an Inter-Office Messaging Application, IOMA. This application will be installed by the users to communicate with each other while

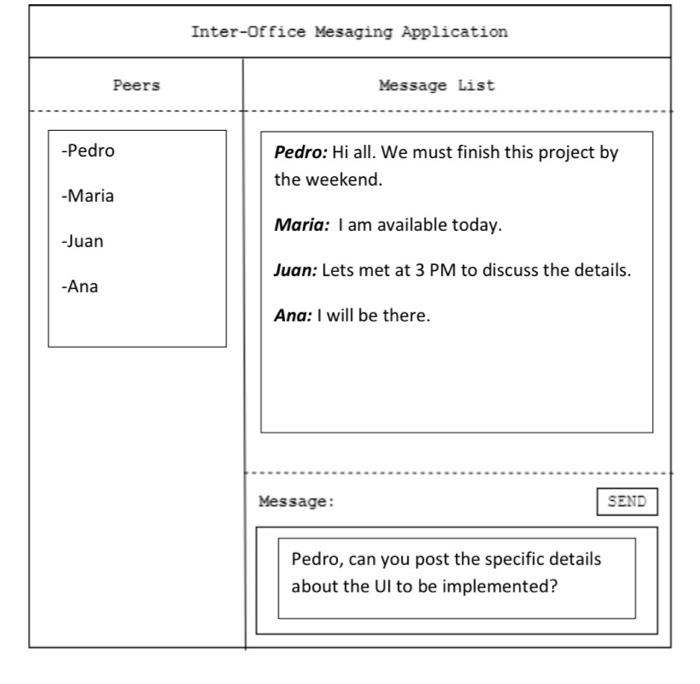

Design Project Description - Inter-Office Messaging Application Your team is tasked with developing an Inter-Office Messaging Application, IOMA. This application will be installed by the users to communicate with each other while physically at the office building. Your team must implement a hybrid P2P architecture, in which a server is used to register and locate the peers, allowing them to communicate with each other via a P2P format. The user application should be able to identify all other peers currently in the network and send and receive messages to them. It must save each of the sent and received messages, with an option to download them to a file. All conversations between peers are to be encrypted, your team must decide the encryption algorithm to be used. The application uses UDP as its Transport layer protocol, so it must be capable of handling transmission crrors, retransmissions, buffers and queues. Dawalan simala GuLforniti in othmatimit the shown in the imam hal Inter-office Mesaging Application Peers Message List - Pedro Pedro: Hi all. We must finish this project by the weekend. -Maria Maria: I am available today. -Juan Juan: Lets met at 3 PM to discuss the details. -Ana Ana: I will be there. Message: SEND Pedro, can you post the specific details about the UI to be implemented? Done WI-20_IOMA (29 of 29) The application creates a UDP socket and uses port number 40,000 for the server, and port number 50,000 for the peers. The server MUST listen to the broadcast address and be bind to its assigned IP address. Each user must first contact the server to register and get a list of the peers. The server will broadcast a message to all users whenever a new user enters, or leaves, the network This message includes each user's IP address and registered username. Peers send messages to each other directly using a unicast message; the server is not used as a relay. The user application must signal the server when it leaves the network. Follow the Engineering Design Process to provide an accurate and implementable solution. DO NOT COPY other code without the proper acknowledgement. Your team is required to develop the code for the applications; hence your submission must be an original program Develop a presentation in which the team confirms that the solution works. The presentation must show how all requirements are satisfied. During the presentation, a live demonstration of the application is expected Your team must also develop a complete written report which showcases how the Engineering Design Process was used to develop and implement the solution and the well commented source Design Project Description - Inter-Office Messaging Application Your team is tasked with developing an Inter-Office Messaging Application, IOMA. This application will be installed by the users to communicate with each other while physically at the office building. Your team must implement a hybrid P2P architecture, in which a server is used to register and locate the peers, allowing them to communicate with each other via a P2P format. The user application should be able to identify all other peers currently in the network and send and receive messages to them. It must save each of the sent and received messages, with an option to download them to a file. All conversations between peers are to be encrypted, your team must decide the encryption algorithm to be used. The application uses UDP as its Transport layer protocol, so it must be capable of handling transmission crrors, retransmissions, buffers and queues. Dawalan simala GuLforniti in othmatimit the shown in the imam hal Inter-office Mesaging Application Peers Message List - Pedro Pedro: Hi all. We must finish this project by the weekend. -Maria Maria: I am available today. -Juan Juan: Lets met at 3 PM to discuss the details. -Ana Ana: I will be there. Message: SEND Pedro, can you post the specific details about the UI to be implemented? Done WI-20_IOMA (29 of 29) The application creates a UDP socket and uses port number 40,000 for the server, and port number 50,000 for the peers. The server MUST listen to the broadcast address and be bind to its assigned IP address. Each user must first contact the server to register and get a list of the peers. The server will broadcast a message to all users whenever a new user enters, or leaves, the network This message includes each user's IP address and registered username. Peers send messages to each other directly using a unicast message; the server is not used as a relay. The user application must signal the server when it leaves the network. Follow the Engineering Design Process to provide an accurate and implementable solution. DO NOT COPY other code without the proper acknowledgement. Your team is required to develop the code for the applications; hence your submission must be an original program Develop a presentation in which the team confirms that the solution works. The presentation must show how all requirements are satisfied. During the presentation, a live demonstration of the application is expected Your team must also develop a complete written report which showcases how the Engineering Design Process was used to develop and implement the solution and the well commented source
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


