Question: Examine the two applications shown in Figures 8-9a and 8-9b. Identify the various security considerations that are relevant to each environment.? (a) Static page request
Examine the two applications shown in Figures 8-9a and 8-9b. Identify the various security considerations that are relevant to each environment.?
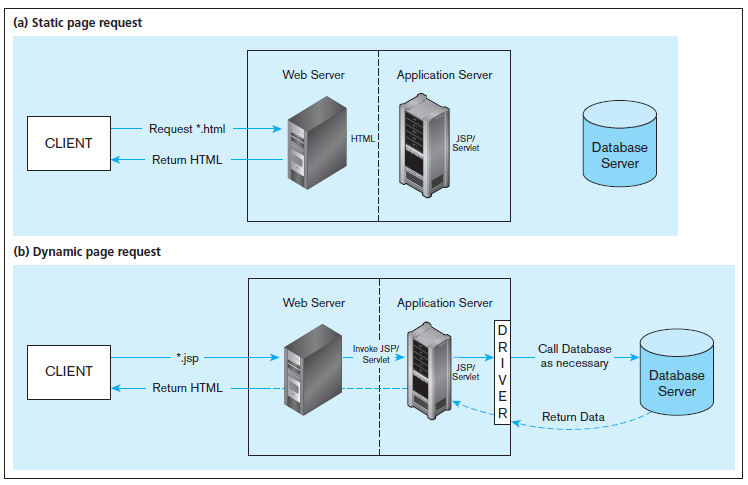
(a) Static page request Web Server Application Server Request *.html HTML CLIENT JSP/ Serviet Database Return HTML Server (b) Dynamic page request Web Server Application Server Invoke JSP/ Call Database Servlet as necessary dsf. JSP/ CLIENT Servlet Database Return HTML Server Return Data OR-> ER
Step by Step Solution
3.51 Rating (171 Votes )
There are 3 Steps involved in it
In the context of a simple static page request to a web server the security risks are associated mos... View full answer

Get step-by-step solutions from verified subject matter experts
Document Format (1 attachment)
613-CS-DB (2059).docx
120 KBs Word File


