Question: Modify Table 10-1 web site for to indicate whether each control listed there is preventive, detective, or corrective in nature. 10.2Table 10-1 suggests that restricting
Modify Table 10-1 web site for to indicate whether each control listed there is preventive, detective, or corrective in nature.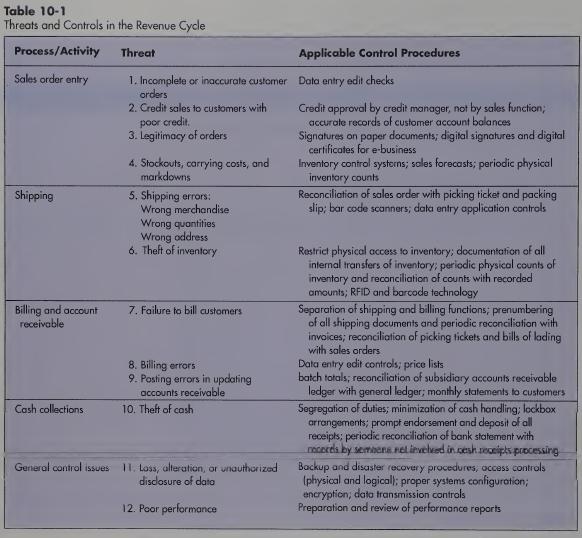
10.2Table 10-1 suggests that restricting physical access to inventory is one way to reduce the threat of theft. Describe specific ways to use information technology to accomplish that objective.
10.3What internal control procedure(s) would provide protection against the following threats? If more than one control procedure could be used to solve a problem, rank the alternatives in terms of their effectiveness.
a. Theft of goods by the shipping dock workers, who claim that the inventory shortages reflect errors in the inventory records.
b. Posting the sales amount to the wrong customer account because a customer account number was incorrectly keyed into the system.
c. Making a credit sale to a customer who is already four months behind in making payments on his account.
d. Authorizing a credit memo for a sales return when the goods were never actually returned.
e. Writing off a customer’s accounts receivable balance as uncollectible to conceal the theft of subsequent collections.
f. Billing customers for the quantity ordered when the quantity shipped was actually less due to back ordering of some items.
g. Theft of checks by the mailroom clerk, who then endorsed the checks for deposit into the clerk’s personal bank account.
h. Theft of funds by the cashier, who cashed several checks and did not record their receipt.
i. Theft of cash by a waiter who destroyed the customer sales ticket for customers who paid cash.
j. Shipping goods to a customer but then failing to bill that customer.
k. Lost sales because of stockouts of several products for which the computer records indicated there was adequate quantity on hand.
l. Unauthorized disclosure of buying habits of several well-known customers.
m. Loss of all information about amounts owed by customers in New York City because the master database for that office was destroyed in a fire.
n. The company’s Web site was unavailable for seven hours because of a power outage.
o. Interception and theft of customers’ credit card numbers while being sent to the company’s Web site.
p. A sales clerk sold a $7,000 wide-screen TV to a friend and altered the price to $700.
q. A shipping clerk who was quitting to start a competing business copied the names of the company’s 500 largest customers and offered them lower prices and better terms if they purchased the same product from the clerk’s new company.
r. The company’s main server crashed and destroyed all the files on the hard disk. Backup copies were used to restore the database on a new server, but the backup did not contain information about any sales made during the past three days.
s. A fire in the office next door damaged the company’s servers and all optical and magnetic media in the server room. The company immediately implemented its disaster recovery procedures and shifted to a backup center several miles away. The company had made full daily backups of all files and stored a copy at the backup center. However, none of the backup copies were readable.
10.4EXCEL PROJECT. (Hint: For help on steps b and
c, see the article “Dial a Forecast,” by James A. Weisel, in the December 2006 issue of the Journal of Accountancy. The Journal of Accountancy is available in print or online at the AICPA’s Web site: www.aicpa.org).
a. Create a 12-month cash budget in Excel using the following assumptions:
• Initial sales of $5,000,000 with forecasted monthly growth of 1%
• 40% of each month’s sales for cash; 30% collected the following month; 20% collected 2 months later; 8% collected 3 months later; and 2% never collected • Initial cash balance of $350,000.
b. Add a “spinner” to your spreadsheet that will enable you to easily change fore¬ casted monthly sales growth to range from 0.5% to 1.5% in increments of 0.1%.
c. Add a scroll bar to your spreadsheet that will let you modify the amount of ini¬ tial sales to vary from $4,000,000 to $6,000,000 in increments of $100,000.
d. Design appropriate data entry and processing controls to ensure spreadsheet accuracy.
Table 10-1 Threats and Controls in the Revenue Cycle Process/Activity Sales order entry Shipping Billing and account receivable Cash collections General control issues Threat Applicable Control Procedures 1. Incomplete or inaccurate customer Data entry edit checks orders 2. Credit sales to customers with poor credit. 3. Legitimacy of orders 4. Stockouts, carrying costs, and markdowns 5. Shipping errors: Wrong merchandise Wrong quantities Wrong address 6. Theft of inventory 7. Failure to bill customers 8. Billing errors 9. Posting errors in updating accounts receivable 10. Theft of cash 11. Loss, alteration, or unauthorized disclosure of data 12. Poor performance Credit approval by credit manager, not by sales function; accurate records of customer account balances Signatures on paper documents; digital signatures and digital certificates for e-business Inventory control systerns; sales forecasts; periodic physical inventory counts Reconciliation of sales order with picking ticket and packing slip; bar code scanners; data entry application controls Restrict physical access to inventory; documentation of all internal transfers of inventory; periodic physical counts of inventory and reconciliation of counts with recorded amounts; RFID and barcode technology Separation of shipping and billing functions; prenumbering of all shipping documents and periodic reconciliation with invoices; reconciliation of picking tickets and bills of lading with sales orders Data entry edit controls; price lists batch totals; reconciliation of subsidiary accounts receivable ledger with general ledger; monthly statements to customers Segregation of duties; minimization of cash handling; lockbox arrangements; prompt endorsement and deposit of all receipts; periodic reconciliation of bank statement with receres by semena net invelved in cesh receipts processing Backup and disaster recovery procedures, access controls (physical and logical); proper systems configuration; encryption; data transmission controls Preparation and review of performance reports
Step by Step Solution
3.40 Rating (147 Votes )
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


