Question: Referring to Appendix 9A, distinguish among data encryption, public key cryptography, and digital signatures. Appendix 9A Public Key Cryptography and Digital Signatures As we noted
Referring to Appendix 9A, distinguish among data encryption, public key cryptography, and digital signatures.

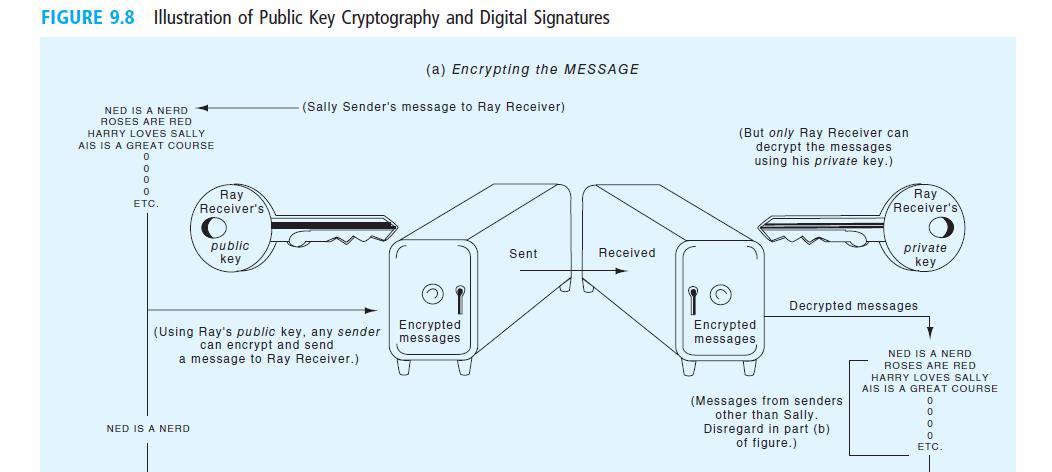
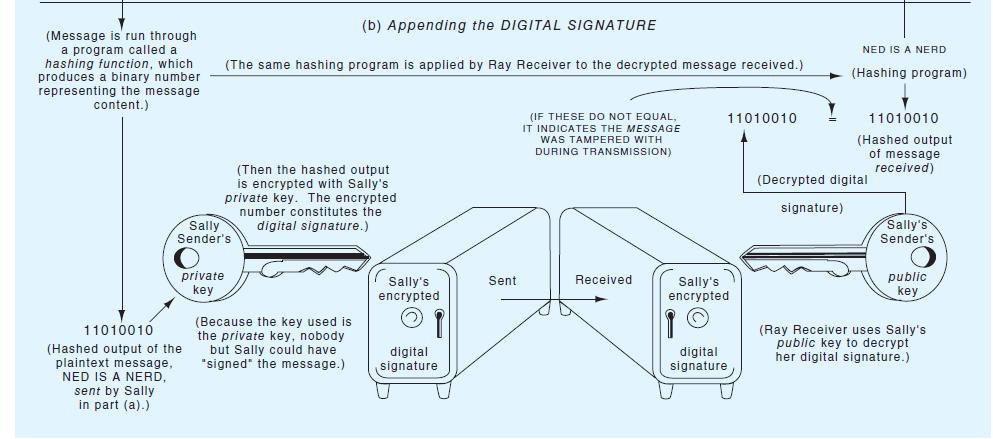
Appendix 9A Public Key Cryptography and Digital Signatures As we noted in Chapter 8, a conventional data encryption procedure involves a single key that is used both by the sender to encrypt the message and by the receiver to decrypt it. A major drawback to single key systems is that you need a different key for each trading partner. Another disadvantage is that the key itself has to be transmitted by secure chan- nels. If the key is not kept secret, the security of the entire system is compromised. Pub- lic key cryptography helps to solve this problem by employing a pair of matched keys for each system user, one private (i.e., known only to the party who possesses it) and one
Step by Step Solution
3.40 Rating (156 Votes )
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


