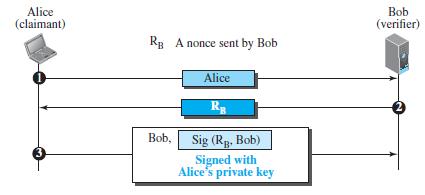
Question: Explain why encryption is used in the second message (from Bob to Alice) in Figure 31.23, but signing is done in the third message (from
Explain why encryption is used in the second message (from Bob to Alice) in Figure 31.23, but signing is done in the third message (from Alice to Bob) in Figure 31.24.
Figure 31.23
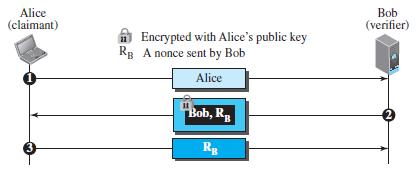
Figure 31.24
Alice (claimant) Bob (verifier) A Encrypted with Alice's public key Rg A nonce sent by Bob Alice Bob, R 3 Rg
Step by Step Solution
3.37 Rating (172 Votes )
There are 3 Steps involved in it
In Figure 3123 Bob encrypts the message with Alices public key encryption should ... View full answer

Get step-by-step solutions from verified subject matter experts


