In a transposition cipher the encryption and decryption keys are often represented as two one-dimension tables (arrays)
Question:
In a transposition cipher the encryption and decryption keys are often represented as two one-dimension tables (arrays) and the cipher is represented as a piece of software (a program).
a. Show the array for the encryption key in Figure 31.6 in the text.
b. Show the array for the decryption key in Figure 31.6 in the text.
Figure 31.6
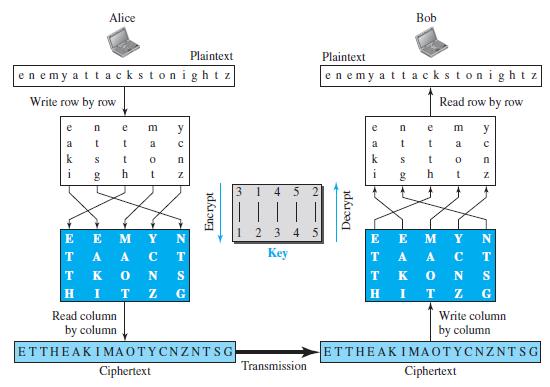
c. Explain, given the encryption key, how we can find the decryption key.
Transcribed Image Text:
Alice Bob Plaintext Plaintext enemy attackstonightz enemy attackstonight z Write row by row Read row by row e e m y m y a a a k k h i h 3. 4 5 123 4 5 E E TA A T K E E M T Кey A A. S T. K H G Read column Write column by column by column ETTHEAKIMAOTYCNZNTSG ETTHEAK IMAOTYCNZNTSG Transmission Ciphertext Ciphertext Z N OT Decrypt Encrypt NZ
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 85% (14 reviews)
The content of each element represents the input col...View the full answer

Answered By

Hassan Imtiaz
The following are details of my Professional Experience. Responsibilities Eight years of demanding teaching experience in the field of finance and business studies at Master’s Level. Completion of the given tasks within given time with quality and efficiency. Marketing professional with practical experience in and solid understanding of a diverse range of management applications, including market analysis, sales and marketing, team building and quality assurance. I have excellent skills to approach deal and sustain corporate clients / customers by demonstrating not only extraordinary communication and interpersonal skills but also high caliber presentation, negotiation and closing skills. Manage and follow up the day-to-day activities. Manage and co-ordinate the inventories. Fulfillment of all the tasks assigned.
The following are details of my Areas of Effectiveness. Finance 1. Corporate Finance 2. Advanced Corporate Finance 3. Management of Financial Institutions 4. International Financial Management 5. Investments 6. Fixed Income 7. Real Estate Investment 8. Entrepreneurial Finance 9. Derivatives 10. Alternative Investments 11. Portfolio Management 12. Financial Statement Analysis And Reporting (US GAAP & IFRS) 13. International Financial Markets 14. Public Finance 15. Personal finance 16. Real estate 17. Financial Planning Quantitative Analysis 1. Time Value Of Money 2. Statistics 3. Probability Distribution 4. Business Statistics 5. Statistical Theory and Methods Economics 1. Principles of Economics 2. Economic Theory 3. Microeconomic Principles 4. Macroeconomic Principles 5. International Monetary Economics 6. Money and Banking 7. Financial Economics 8. Population Economics 9. Behavioral Economics International Business 1. Ethics 2. Business Ethics 3. An introduction to business studies 4. Organization & Management 5. Legal Environment of Business 6. Information Systems in Organizations 7. Operations Management 8. Global Business Policies 9. Industrial Organization 10. Business Strategy 11. Information Management and Technology 12. Company Structure and Organizational Management Accounting & Auditing 1. Financial Accounting 2. Managerial Accounting 3. Accounting for strategy implementation 4. Financial accounting 5. Introduction to bookkeeping and accounting Marketing 1. Marketing Management 2. Professional Development Strategies 3. Business Communications 4. Business planning 5. Commerce & Technology Human resource management 1. General Management 2. Conflict management 3. Leadership 4. Organizational Leadership 5. Supply Chain Management 6. Law 7. Corporate Strategy Creative Writing 1. Analytical Reading & Writing Other Expertise 1. Risk Management 2. Entrepreneurship 3. Management science 4. Organizational behavior 5. Project management 6. Financial Analysis, Research & Companies Valuation 7. And any kind of Excel Queries
4.80+
150+ Reviews
230+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
Alice and Bob exchange confidential messages. They share a very large number as the encryption and decryption key in both directions. Is this an example of symmetric-key or asymmetric-key...
-
A general program to implement transposition cipher (encryption and decryption). The input to the program is a flag that demands encryption or decryption, the symmetric key, and the plaintext or...
-
A general program to implement substitution (additive) cipher (encryption and decryption). The input to the program is a flag that demands encryption or decryption, the symmetric key, and the...
-
Perform computational experiments to verify that the average path length in a ring graph on \(V\) vertices is \(\sim 1 / 4 V\). Then, repeat these experiments, but add one random edge to the ring...
-
Differentiate between ordinary and subliminal advertising using examples to illustrate.
-
A study reported in the medical journal Fertility and Sterility sought to determine whether the ancient Chinese art of acupuncture could help infertile women become pregnant. A total of 160 healthy...
-
Consider the Michaelis-Menten model introduced in Eq. (12.23). Graph the expectation function for this model for \(\theta_{1}=200\) and \(\theta_{2}=0.04,0.06,0.08\), 0.10 . Overlay these curves on...
-
Casey Carpet manufactures broadloom carpet in seven processes: spinning, dyeing, plying, spooling, tufting, latexing, and shearing. In the Dyeing Department, direct materials (dye) are added at the...
-
Pitch a recommendation to a company of your choosing with your prediction of the potential success or downfall of Facebook and the MetaVerse for social media marketing. Essentially, would you...
-
Suellen Symmes died on January 15, 2022. Her estate elected a November 30 year end. The executor projects that the estate will receive interest income of $50,000 by November 30, 2022, and will have...
-
In a cipher, all As in the plaintext have been changed to Ds in the ciphertext and all Ds in the plaintext have been changed to Hs in the ciphertext. Is this a monoalphabetic or polyalphabetic...
-
Distinguish between a substitution cipher and a transposition cipher.
-
Show that the total transaction costs in Lelands model (Leland, 1985) increases (decreases) with the strike price X when X (X > X ), where X* = Ser+2)(T-1) S (1-164 o Use the result()=/27 d exp(-).
-
Hicham El Guerrouj of Morocco holds the world record in the 1500 m running race. He ran the final 400 m in a time of 51.9 s. What was his average speed in mph over the last 400 m? A. 14.2 mph B. 15.5...
-
Based on MM propositions with corporate taxes, what is Bemas weighted average cost of capital after the completion of their announced debt-financed share repurchase program? A. 6.52%. B. 7.83%. C....
-
Mark and Sofia walk together down a long, straight road. They walk without stopping for 4 miles. At this point Sofia says their displacement during the trip must have been 4 miles; Mark says their...
-
If a companys operating profit margin is 4% and its total asset turnover is 1.5 times, its operating return on assets is: A. 2.7%. B. 6.0%. C. 7.3%.
-
What is the impulse on a \(3.0 \mathrm{~kg}\) particle that experiences the force described by the graph in Figure P9.38? F, (N) 1500 1000 500 0 (ms) 24 8 10 -500 -1000 FIGURE P9.38
-
Suppose you were hired to design an automatic irrigating system for a wealthy homeowner's garden. You determine that the flower beds should be kept at a water potential above -60 kPa, but not wetter...
-
Outline some of the major problems confronting an international advertiser.
-
State whether each of the following is true or false. If false, explain why. a) An algorithm is a procedure for solving a problem in terms of the actions to execute and the order in which these...
-
Write four different C# statements that each add 1 to int variable x.
-
Write C# statements to accomplish each of the following tasks: a) Assign the sum of x and y to z, and increment x by 1 with ++. Use only one statement and ensure that the original value of x is used...
-
Victor Korchnoi bought a bond one month before a semi-annual coupon was due. The face value was $10,000 and the coupon rate 8.5%. At the time of purchase there were 34 coupons left and the YTM was 6%...
-
4. Consider a 30-year U.S. Treasury bond paying 4.5 percent coupon, and selling for $1010. What is the yield to maturity? Make sure to show your work. 5. A 30-year U.S. corporate bond with a 6...
-
A project's base case or most likely NPV is $44,000, and assume its probability of occurrence is 50%. Assume the best-case scenario NPV is 65% higher than the base case and assume the worst scenario...

Study smarter with the SolutionInn App


