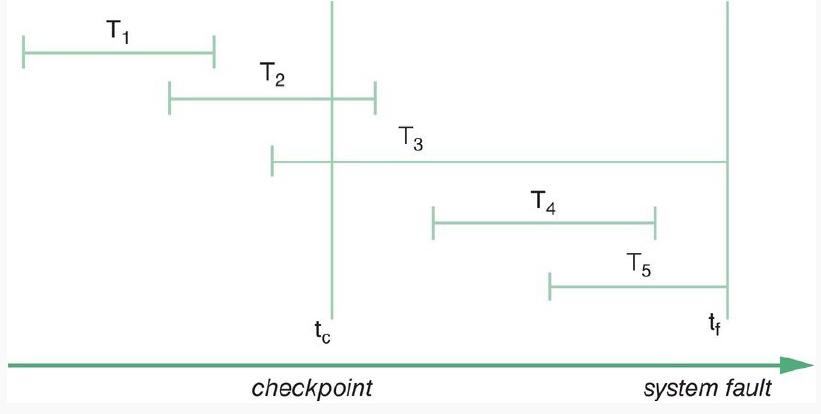
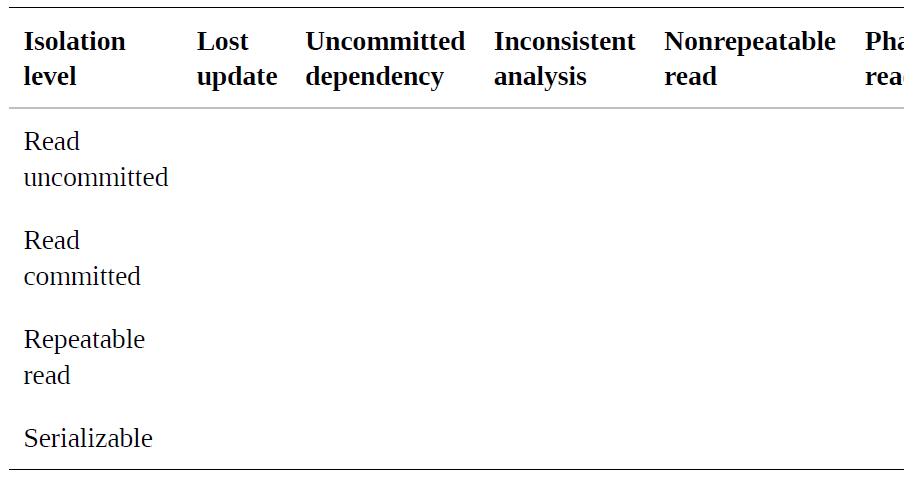
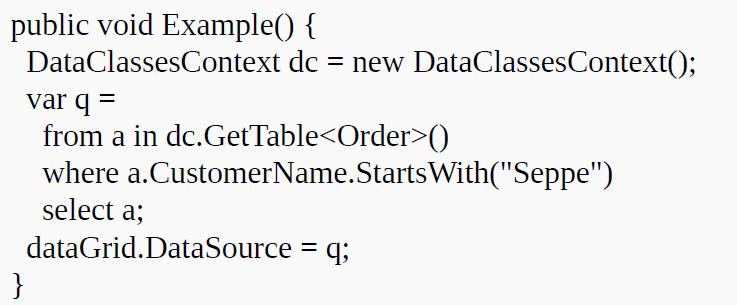
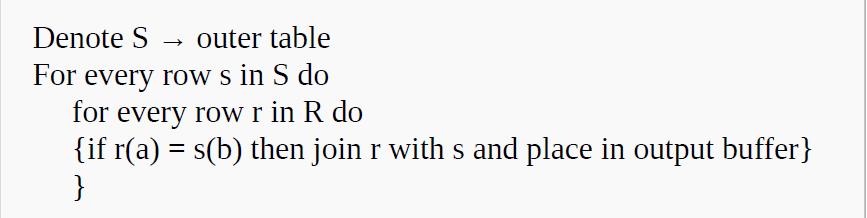![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()



![OPTIONAL MATCH (user: User)-[:FRIENDS_WITH]- (friend: User) WHERE user.name = "Bart Baesens" RETURN user,](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1702/6/2/7/994657c0a9a9e4471702627993091.jpg)