Question: You are given the task of patching the vulnerability in the XDR code shown in the aside on page 136 for the case where both
You are given the task of patching the vulnerability in the XDR code shown in the aside on page 136 for the case where both data types int and size_t are 32 bits. You decide to eliminate the possibility of the multiplication overflowing by computing the number of bytes to allocate using data type uint64_t. You replace the original call to malloc (line 9) as follows:
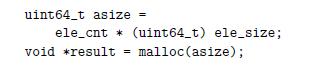
Recall that the argument to malloc has type size_t.
A. Does your code provide any improvement over the original?
B. How would you change the code to eliminate the vulnerability?
uint64_t asize ele_cnt* (uint64_t) ele_size; malloc (asize); void *result =
Step by Step Solution
3.46 Rating (149 Votes )
There are 3 Steps involved in it
A This change does not help at all Even though the computation of a size will ... View full answer

Get step-by-step solutions from verified subject matter experts


