Question: Assume you are a midlevel systems administrator for one section of a larger organization. You try to encourage your users to have good password policies
Assume you are a midlevel systems administrator for one section of a larger organization.
You try to encourage your users to have good password policies and you regularly run password-cracking tools to check that those in use are not guessable. You have become aware of a burst of hacker password-cracking activity recently. In a burst of enthusiasm you transfer the password files from a number of other sections of the organization and attempt to crack them. To your horror, you find that in one section for which you used to work (but now have rather strained relationships with), something like 40% of the passwords are guessable (including that of the vicepresident of the section, whose password is “pre$ident”!). You quietly sound out a few former colleagues and drop hints in the hope things might improve.A couple of weeks later you again transfer the password file over to analyze in the hope things have improved.They haven’t. Unfortunately, this time one of your colleagues notices what you are doing. Being a rather “by the book” person, he notifies senior management, and that evening you find yourself being arrested on a charge of hacking and thrown out of a job. Did you do anything wrong? Which of the potential ethical dilemmas listed in Table 23.3 does this case illustrate? Briefly indicate what arguments you might use to defend your actions, Make reference to the Professional Codes of Conduct shown in Figures 23.7 through 23.9. 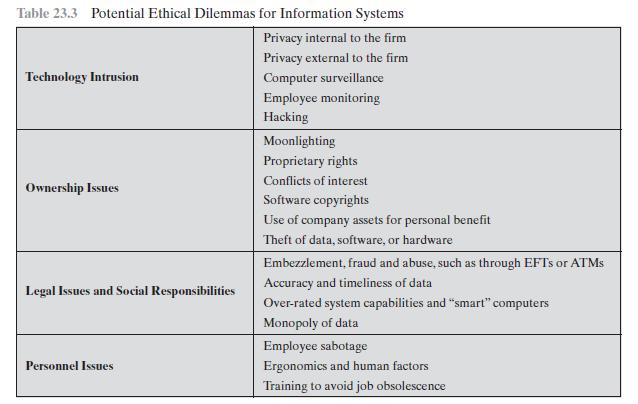
Figure 23.7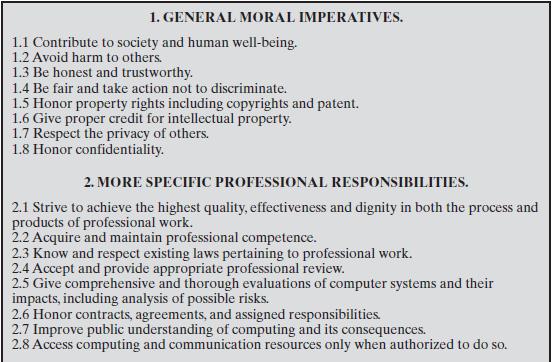
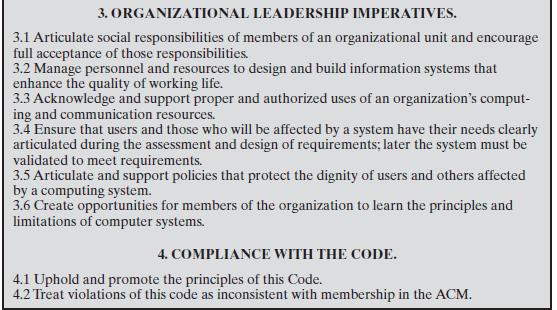
Table 23.3 Potential Ethical Dilemmas for Information Systems Privacy internal to the firm Privacy external to the firm Computer surveillance Employee monitoring Hacking Technology Intrusion Ownership Issues Legal Issues and Social Responsibilities Personnel Issues Moonlighting Proprietary rights Conflicts of interest Software copyrights Use of company assets for personal benefit Theft of data, software, or hardware Embezzlement, fraud and abuse, such as through EFTs or ATMs Accuracy and timeliness of data Over-rated system capabilities and "smart" computers Monopoly of data Employee sabotage Ergonomics and human factors Training to avoid job obsolescence
Step by Step Solution
3.34 Rating (145 Votes )
There are 3 Steps involved in it
In this scenario the administrator has very likely broken the law though it depends on the jurisdict... View full answer

Get step-by-step solutions from verified subject matter experts


