Question: Consider a one-way authentication technique based on asymmetric encryption: a. Explain the protocol. b. What type of attack is this protocol susceptible to? A B:
Consider a one-way authentication technique based on asymmetric encryption: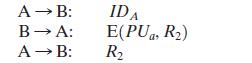
a. Explain the protocol.
b. What type of attack is this protocol susceptible to?
A B: B A: A B: IDA E(PUa, R) R
Step by Step Solution
3.35 Rating (161 Votes )
There are 3 Steps involved in it
a This is a means of authenticating A to B Only A c... View full answer

Get step-by-step solutions from verified subject matter experts


