Question: End-to-end authentication and encryption are desired between two hosts. Draw figures similar to Figure 19.8 that show each of the following. a. Transport adjacency with
End-to-end authentication and encryption are desired between two hosts. Draw figures similar to Figure 19.8 that show each of the following.
a. Transport adjacency with encryption applied before authentication.
b. A transport SA bundled inside a tunnel SA with encryption applied before authentication.
c. A transport SA bundled inside a tunnel SA with authentication applied before encryption.
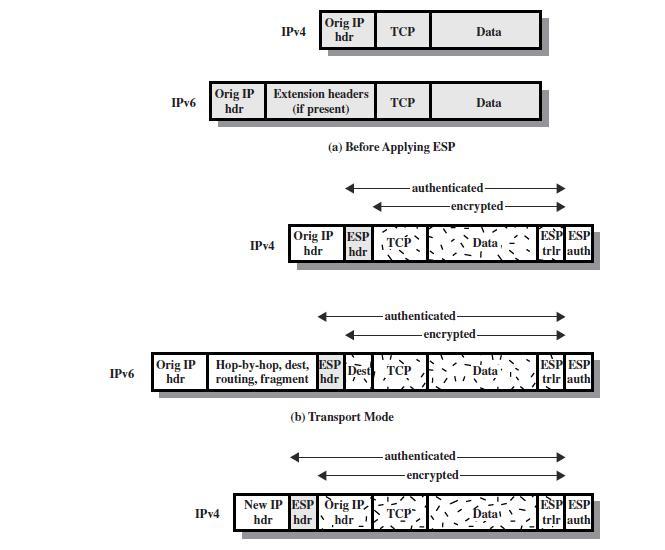
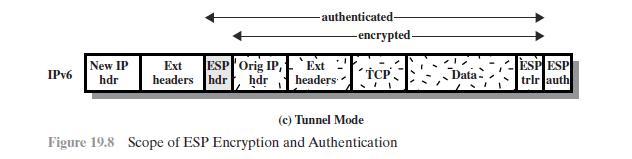
IPv6 IPv6 Orig IP hdr Orig IP hdr IPv4 IPv4 IPv4 Orig IP hdr Extension headers (if present) Orig IP ESP hdr hdr TCP (a) Before Applying ESP TCP New IP ESP Orig IP, hdr hdr hdr Tcp Hop-by-hop, dest, ESP Dest TCP routing, fragment hdr (b) Transport Mode -authenticated- authenticated- Data TCP Data -encrypted- -authenticated- -encrypted- Data, -encrypted- Data ata ESP ESP trlr auth ESP ESP trir auth ESP ESP trir auth
Step by Step Solution
3.31 Rating (151 Votes )
There are 3 Steps involved in it
We show ... View full answer

Get step-by-step solutions from verified subject matter experts


