Question: Repeat Problem 23.1 for Table 23.2. Table 23.2 CERT 2006 E-Crime Watch Survey Results Theft of intellectual property Theft of other (proprietary) info including customer
Repeat Problem 23.1 for Table 23.2.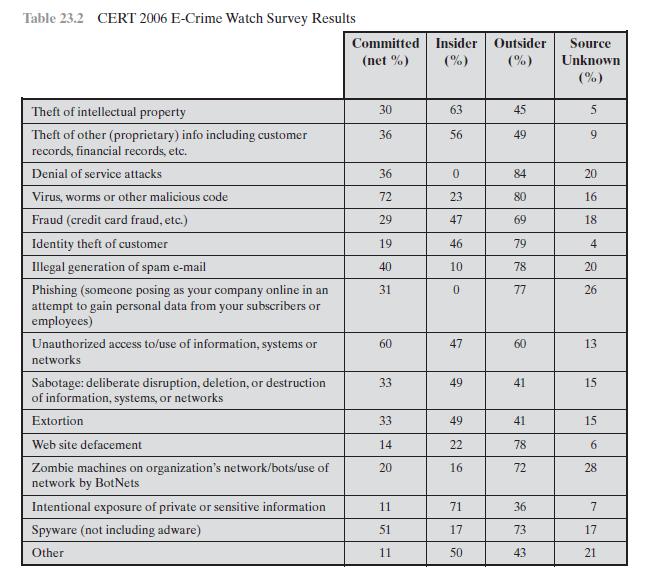
Table 23.2 CERT 2006 E-Crime Watch Survey Results Theft of intellectual property Theft of other (proprietary) info including customer records, financial records, etc. Denial of service attacks Virus, worms or other malicious code Fraud (credit card fraud, etc.) Identity theft of customer Illegal generation of spam e-mail Phishing (someone posing as your company online in an attempt to gain personal data from your subscribers or employees) Unauthorized access to/use of information, systems or networks Sabotage: deliberate disruption, deletion, or destruction of information, systems, or networks Extortion Web site defacement Zombie machines on organization's network/bots/use of network by BotNets Intentional exposure of private or sensitive information Spyware (not including adware) Other Committed (net %) 30 36 36 72 29 19 40 31 60 33 33 14 20 11 51 11 Insider Outsider Source (%) (%) Unknown (%) 63 56 0 23 47 46 10 0 47 49 49 22 16 71 17 50 45 49 84 80 69 79 78 77 60 41 41 78 72 36 73. 43 5 9 20 16 18 4 20 26 13. 15 15 6 28 7 17 21
Step by Step Solution
3.44 Rating (170 Votes )
There are 3 Steps involved in it
Theft of intellectual property Computer as target attack on data confidentiality Theft of other prop... View full answer

Get step-by-step solutions from verified subject matter experts


