Question: Consider the Java program shown in Figure 10.8. Assume that this is to be compiled to native code on a machine with 4-byte addresses. Figure
Consider the Java program shown in Figure 10.8. Assume that this is to be compiled to native code on a machine with 4-byte addresses.
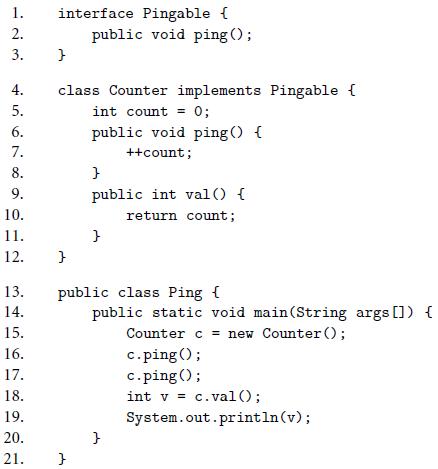
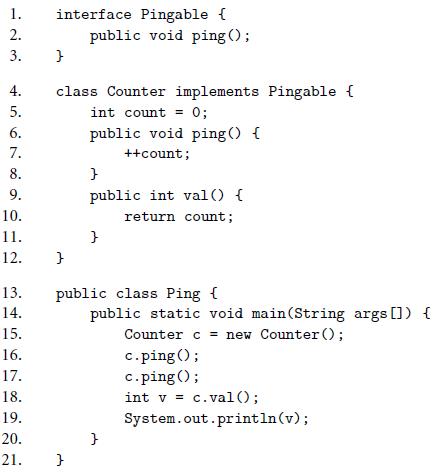
Figure 10.8
(a) Draw a picture of the layout in memory of the object created at line 15. Show all virtual function tables.
(b) Give assembly-level pseudocode for the call to c.val at line 19. You may assume that the address of c is in register r1 immediately before the call, and that this same register should be used to pass the hidden this parameter. You may ignore the need to save and restore registers, and don’t worry about where to put the return value.
(c) Give assembly-level pseudocode for the call to c.ping at line 17. Again, assume that the address of c is in register r1, that this is the same register that should be used to pass this, and that you don’t need to save or restore any registers.
(d) Give assembly-level pseudocode for the body ofmethod Counter.ping (again ignoring register save/restore).
interface Pingable { public void ping (); 1. 2. 3. 4. class Counter implements Pingable { 5. int count = 0; %3! 6. public void ping() { 7. ++count; 8. 9. public int val () { 10. return count; 11. 12. 13. public class Ping ( 14. public static void main(String args []) { Counter c = new Counter (); c.ping(); c.ping (); 15. 16. 17. 18. int v = c.val(); 19. System.out.println(v); 20. 21. }
Step by Step Solution
3.43 Rating (159 Votes )
There are 3 Steps involved in it
a b c in r1 r2 r1 Counter vtable call r28 invoke val 2nd method c c in r1 r1 8 Pingable v... View full answer

Get step-by-step solutions from verified subject matter experts


