Question: 1. Study G-Schreiber cipher design. Describe known plain-text attack against its internal settings: 1)0-1 distribution on the wheels, 2) wheels initial state, 3) cabling permutation.
1. Study G-Schreiber cipher design. Describe known plain-text attack against its internal settings: 1)0-1 distribution on the wheels, 2) wheels initial state, 3) cabling permutation. The analysis is based on two observations: if the cipher-text 5-bit group is 11111 or 00000 at some moment, then the 5-bit group at the switches input is 11111 or 00000 respectively as well. So one can reconstruct the first 5 bits on the plug for those moments. Therefore the cabling to the first 5 plug positions and 0-1 distribution on related wheels are easily reconstructed by testing periodicity: the period of the bit sequence from a wheel with n =47,53,..,73 positions is n. You know switches input/ output at almost any moment now. Learn about control 5-bit group if switches input/ output comprise single 1 or single 0, that is of weight 1 or 4. Reconstruct the rest of the cabling and 0-1 distribution on related wheels . Remark the bits representing plain-text/cipher-text characters are numbered from left to right. So, for instance, the left most bit of a 5-bit group representing a plain-text character is XORed with the left most bit on the plug. The bottom bit of the output (see the picture) is the left most bit of a 5-bit combination representing the cipher-text character. Also have a look at the Maple implementation provided. 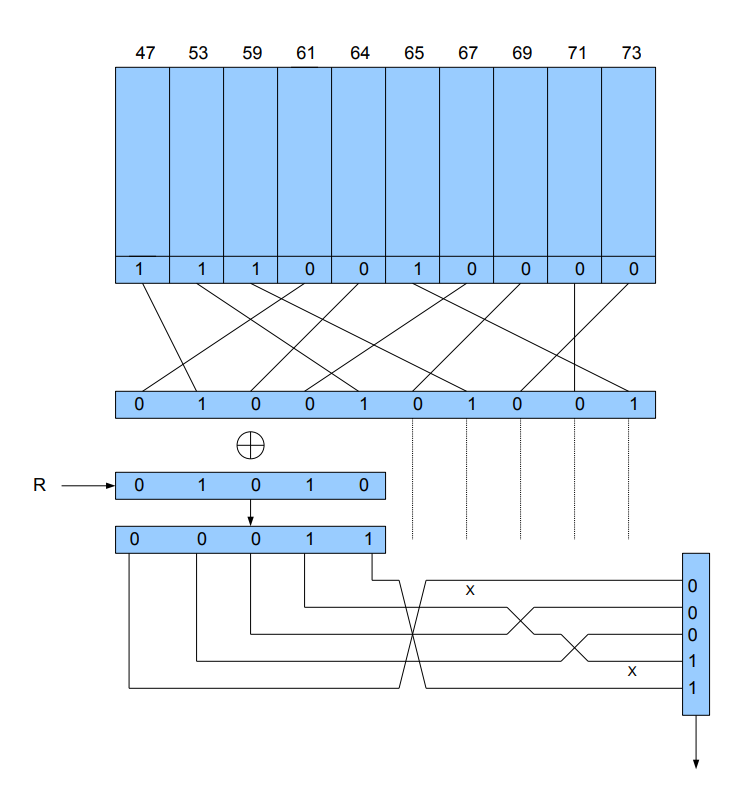
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


