Question: 1) The following process shows authentication method between Alice and Bob. They use asymmetric encryption: (R1 serves as a challenge) (5 points) Bob Alice: Ri
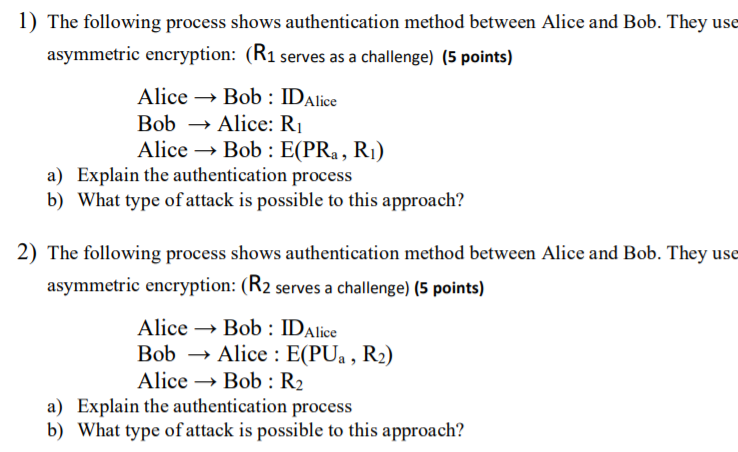
1) The following process shows authentication method between Alice and Bob. They use asymmetric encryption: (R1 serves as a challenge) (5 points) Bob Alice: Ri Alice >Bob: (PRa, Ri) a) Explain the authentication process b) What type of attack is possible to this approach? 2) The following process shows authentication method between Alice and Bob. They use asymmetric encryption: (R2 serves a challenge) (5 points) Alice - Bob : IDAlice BobAlice: E(Pa , R2) Alice Bob : R2 a) Explain the authentication process b) What type of attack is possible to this approach
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


