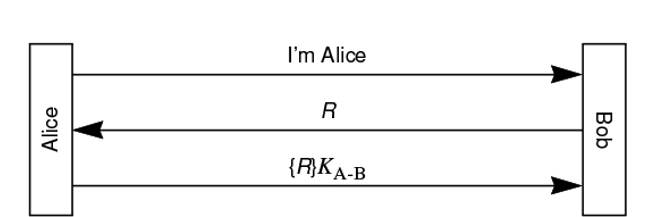
Question: Consider the following authentication protocol. R is the challenge sent by Bob to Alice, and KAB is the secret Alice and Bob share. Which of
Consider the following authentication protocol. R is the challenge sent by Bob to Alice, and KAB is the secret Alice and Bob share. Which of the following are secure for a session key? When answering this question, for each option, think about the three aspects:
a Can Trudy impersonate Alice to Bob?
b Can this session key be securely used to encrypt messages exchanged between Alice and Bob?
c If this session key happened to be known by Trudy, can Trudy find KAB?
To get full credit, for the options that are not secure briefly explain why it is not secure you can explain by giving a case where an attacker can compromise the communication.
d KAB XOR R
e KAB R KAB
fRR KAB
g KAB KAB
hR KAB
i KAB R
Please explain each of them cleary. I also think that only e and f is secured because even if Trudy doesn't know KAB, but KAB already exposed to public from authentication process. It is not secured to only use KAB for encryption like h and g For option d I think Trudy can reverse to know R because XOR is not complex method. Could you please clarify and answer the question for me clearly and in details because I am confused? I am also confused whether option iKABR is secured for session key or not?
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


