Question: 1. Using the CVE database, conduct research on the three high severity vulnerabilities identified by OpenVAS. 2. Using the information gathered during your penetration test
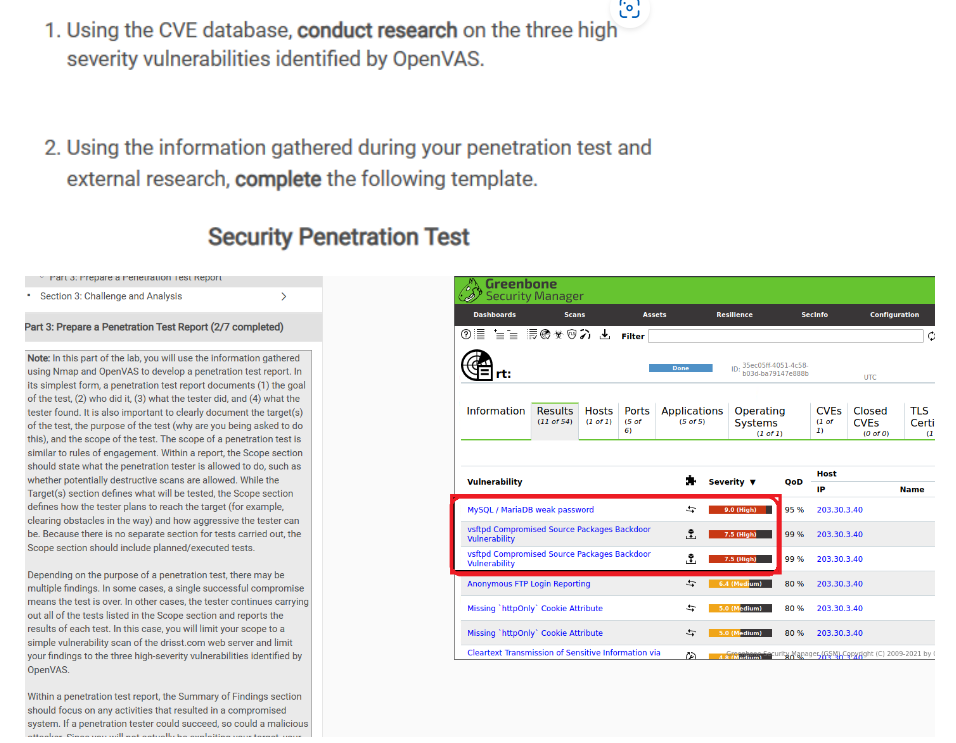
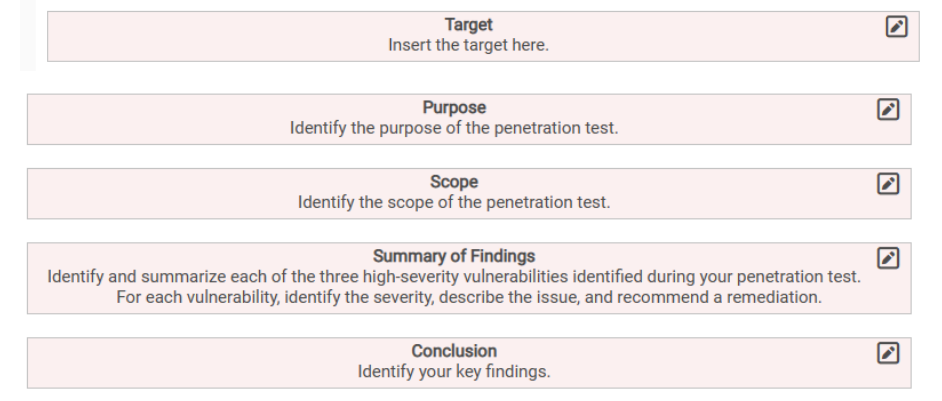
1. Using the CVE database, conduct research on the three high severity vulnerabilities identified by OpenVAS. 2. Using the information gathered during your penetration test and external research, complete the following template. Security Penetration Test Part of prepare a reneuston rest Report Greenbone Section 3: Challenge and Analysis Security Manager Dashboards Scams Assets Resilience Secinto Configuration Part 3: Prepare a Penetration Test Report (2/7 completed) Of 1 50+07 Filter Note: In this part of the lab, you will use the information gathered using Nmap and OpenVAS to develop a penetration test report. In Art: Done D. 35ec05f-4051-4c58 603d-ba79147-BBC UTC its simplest form, a penetration test report documents (1) the goal of the test, (2) who did it, (3) what the tester did, and (4) what the tester found. It is also important to clearly document the target(s) Information Results Hosts Ports Applications Operating VEs Closed TLS of the test, the purpose of the test (why are you being asked to do (11 of 54) 1 of 1) [5 or 5) Systems (1 of CVEs Certi this), and the scope of the test. The scope of a penetration test is (1 of 1 10 of 0) similar to rules of engagement. Within a report, the Scope section should state what the penetration tester is allowed to do, such as Host whether potentially destructive scans are allowed. While the Vulnerability Severity OOD Target(s) section defines what will be tested, the Scope section Name defines how the tester plans to reach the target (for example, MySQL / Maria DB weak password W.0 [ High) 95 % 203.30.3.40 clearing obstacles in the way) and how aggressive the tester can be. Because there is no separate section for tests carried out, the vsftpd Compromised Source Packages Backdoor vulnerability 7.5 High 99 % 203.30.3.40 Scope section should include planned/executed tests. vsitpd Compromised Source Packages Backdoor Vulnerability 7.5 [High] 99 % 203.30.3.40 Depending on the purpose of a penetration test, there may be multiple findings. In some cases, a single successful compromise Anonymous FTP Login Reporting 64 (Medium 80 % 203.30.3.40 means the test is over. In other cases, the tester continues carrying Missing 'httpOnly Cookie Attribute 5.0 (Medium 80 % 203.30.3.40 out all of the tests listed in the Scope section and reports the results of each test. In this case, you will limit your scope to a Missing "httpOnly" Cookie Attribute 30 (Medium 30 % 203.30.3.40 simple vulnerability scan of the drisst. com web server and limit your findings to the three high-severity vulnerabilities identified by Cleartext Transmission of Sensitive Information via amm ling Rages ge:fight IC) 2009-2021 by 1 OpenVAS. Within a penetration test report, the Summary of Findings section should focus on any activities that resulted in a compromised system. If a penetration tester could succeed, so could a maliciousTarget Insert the target here. Purpose Identify the purpose of the penetration test. Scope Identify the scope of the penetration test. Summary of Findings Identify and summarize each of the three high-severity vulnerabilities identified during your penetration test. For each vulnerability, identify the severity, describe the issue, and recommend a remediation. Conclusion Identify your key findings
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


