Question: 10. An even trickier question: In a three-message authentication protocol, Alice initiates contact with Bob. Bob is a stateless server, and thus it is inconvenient
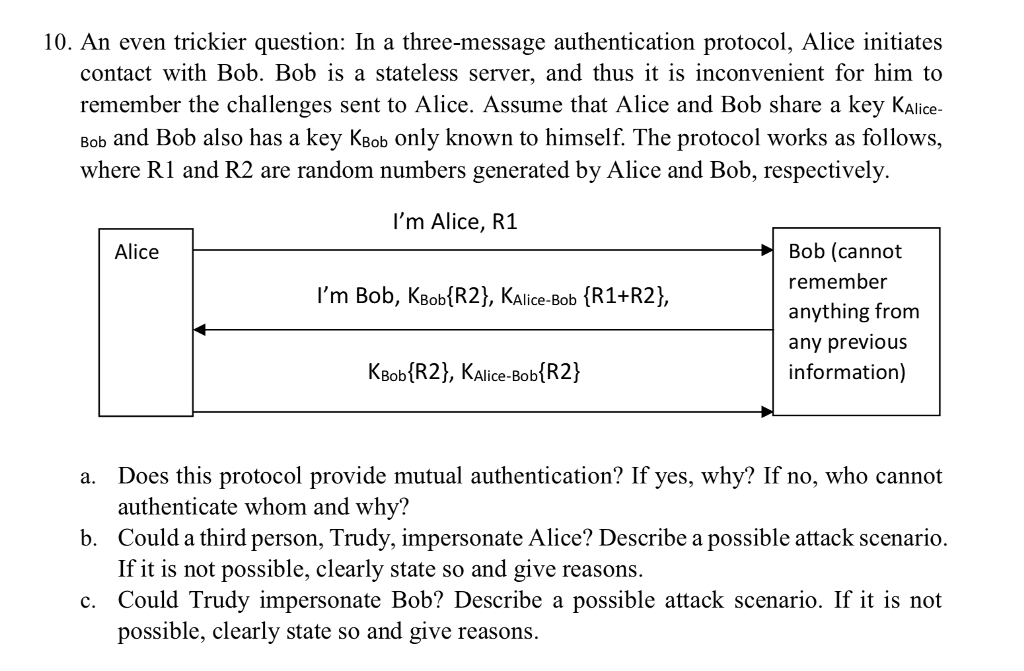
10. An even trickier question: In a three-message authentication protocol, Alice initiates contact with Bob. Bob is a stateless server, and thus it is inconvenient for him to remember the challenges sent to Alice. Assume that Alice and Bob share a key KAlice- Bob and Bob also has a key Ksob only known to himself. The protocol works as follows, where R1 and R2 are random numbers generated by Alice and Bob, respectively. I'm Alice, R1 Bob (cannot remember anything from any previous information) Alice I'm Bob, KBob R2), KAlice-Bob (R1+R2), KBobIR2), Kaice BoblR2) a. Does this protocol provide mutual authentication? If yes, why? If no, who cannot b. Could a third person, Trudy, impersonate Alice? Describe a possible attack scenario. c. Could Trudy impersonate Bob? Describe a possible attack scenario. If it is not authenticate whom and why? If it is not possible, clearly state so and give reasons. possible, clearly state so and give reasons
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


