Question: 18) A security analyst has noticed network traffic coming from an endpoint, which is within the organization's network boundary, to an IP address that is
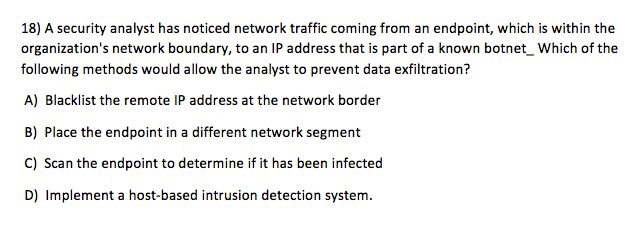
18) A security analyst has noticed network traffic coming from an endpoint, which is within the organization's network boundary, to an IP address that is part of a known botnet_ Which of the following methods would allow the analyst to prevent data exfiltration? A) Blacklist the remote IP address at the network border B) Place the endpoint in a different network segment C) Scan the endpoint to determine if it has been infected D) Implement a host-based intrusion detection system
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


