Question: 18. The %n formatted output modifier in C will write data to a memory location, but in Java a. It is a carriage return. b.
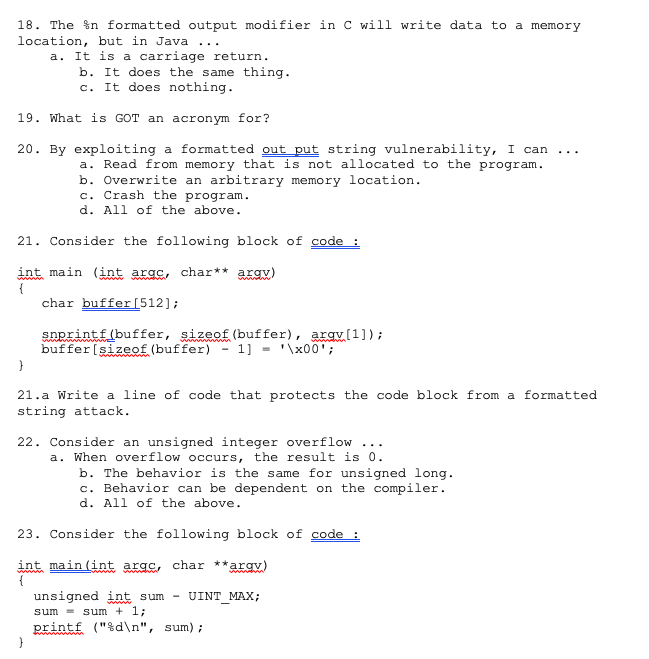
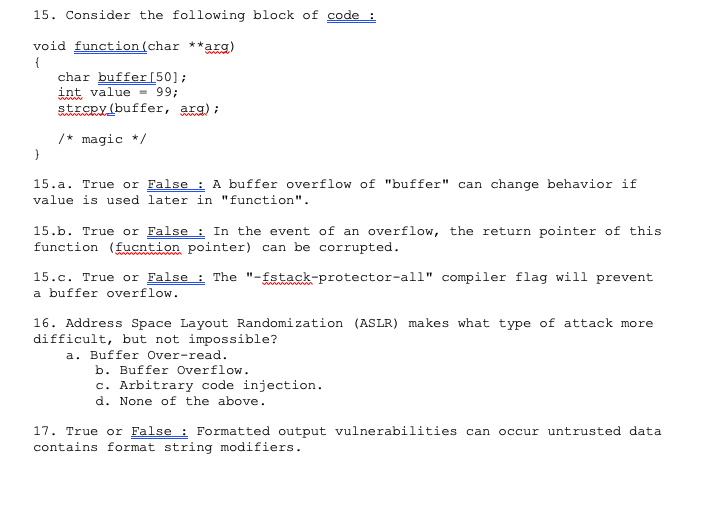
18. The %n formatted output modifier in C will write data to a memory location, but in Java a. It is a carriage return. b. It does the same thing. c. It does nothing 19. What is GOT an acronym for? 20. By exploiting a formatted out put string vulnerability, I can .. . a. Read from memory that is not allocated to the program. b. Overwrite an arbitrary memory location. c. Crash the program. d. All of the above. 21. Consider the following block of code int main (int axgc, char** arav) char bufferI512]; snprintf(buffer, sizeof (buffer), argy.[1]); buffer [sizeof (buffer)-1-'1x00 21.a Write a 1ine of code that protects the code block from a formatted string attack. 22. Consider an unsigned integer overflow a. When overflow occurs, the result is 0. b. The behavior is the same for unsigned long. c. Behavior can be dependent on the compiler d. All of the above. 23. Consider the following block of code int, main(int args, char **arqv) unsigned int sum - UINT_MAX; sum- sum 1; ReansE ("%d ", sum) ; 15. Consider the following block of code void function(char **axg) char buffer[50]; int value -99; stESpyLbuffer, arg) /*magic/ 15.a. True or False A buffer overflow of "buffer" can change behavior if value is used later in "function". 15.b. True or False: In the event of an overflow, the return pointer of this function (fucntion pointer) can be corrupted. 15.c. True or False i The "-fstack-protector-all" compiler flag will prevent a buffer overflow 16. Address Space Layout Randomization (ASLR) makes what type of attack more difficult, but not impossible? a. Buffer Over-read b. Buffer Overflow c. Arbitrary code injection d. None of the above. 17. True or False Formatted output vulnerabilities can occur untrusted data contains format string modifiers. 18. The %n formatted output modifier in C will write data to a memory location, but in Java a. It is a carriage return. b. It does the same thing. c. It does nothing 19. What is GOT an acronym for? 20. By exploiting a formatted out put string vulnerability, I can .. . a. Read from memory that is not allocated to the program. b. Overwrite an arbitrary memory location. c. Crash the program. d. All of the above. 21. Consider the following block of code int main (int axgc, char** arav) char bufferI512]; snprintf(buffer, sizeof (buffer), argy.[1]); buffer [sizeof (buffer)-1-'1x00 21.a Write a 1ine of code that protects the code block from a formatted string attack. 22. Consider an unsigned integer overflow a. When overflow occurs, the result is 0. b. The behavior is the same for unsigned long. c. Behavior can be dependent on the compiler d. All of the above. 23. Consider the following block of code int, main(int args, char **arqv) unsigned int sum - UINT_MAX; sum- sum 1; ReansE ("%d ", sum) ; 15. Consider the following block of code void function(char **axg) char buffer[50]; int value -99; stESpyLbuffer, arg) /*magic/ 15.a. True or False A buffer overflow of "buffer" can change behavior if value is used later in "function". 15.b. True or False: In the event of an overflow, the return pointer of this function (fucntion pointer) can be corrupted. 15.c. True or False i The "-fstack-protector-all" compiler flag will prevent a buffer overflow 16. Address Space Layout Randomization (ASLR) makes what type of attack more difficult, but not impossible? a. Buffer Over-read b. Buffer Overflow c. Arbitrary code injection d. None of the above. 17. True or False Formatted output vulnerabilities can occur untrusted data contains format string modifiers
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


