Question: 2. Implement the cipher using $mathrm{C} ++$ or Java. ( 5 marks) The program should be able to do both encryption and decryption. All characters,
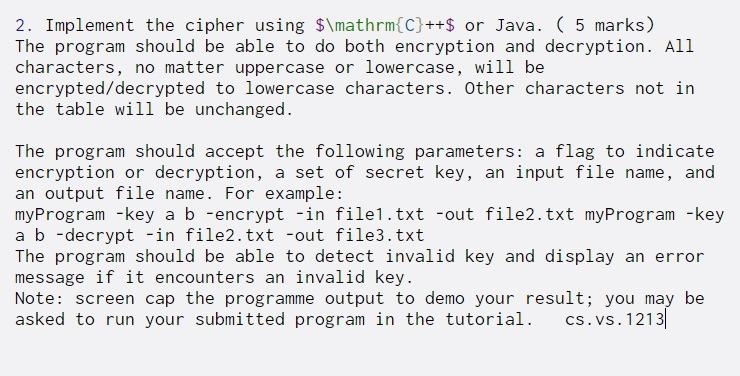
2. Implement the cipher using $\mathrm{C} ++$ or Java. ( 5 marks) The program should be able to do both encryption and decryption. All characters, no matter uppercase or lowercase, will be encrypted/decrypted to lowercase characters. Other characters not in the table will be unchanged. The program should accept the following parameters: a flag to indicate encryption or decryption, a set of secret key, an input file name, and an output file name. For example: myProgram -key a b -encrypt -in file1.txt -out file2.txt my Program -key a b - decrypt -in file2.txt -out file3.txt The program should be able to detect invalid key and display an error message if it encounters an invalid key. Note: screen cap the programme output to demo your result; you may be asked to run your submitted program in the tutorial. cs.vs. 1213 2. Implement the cipher using $\mathrm{C} ++$ or Java. ( 5 marks) The program should be able to do both encryption and decryption. All characters, no matter uppercase or lowercase, will be encrypted/decrypted to lowercase characters. Other characters not in the table will be unchanged. The program should accept the following parameters: a flag to indicate encryption or decryption, a set of secret key, an input file name, and an output file name. For example: myProgram -key a b -encrypt -in file1.txt -out file2.txt my Program -key a b - decrypt -in file2.txt -out file3.txt The program should be able to detect invalid key and display an error message if it encounters an invalid key. Note: screen cap the programme output to demo your result; you may be asked to run your submitted program in the tutorial. cs.vs. 1213
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


