Question: 4) [20 points) The RISC-V code for Procedure Y is shown in the first column of the following table. Procedure X calls Procedure Y and
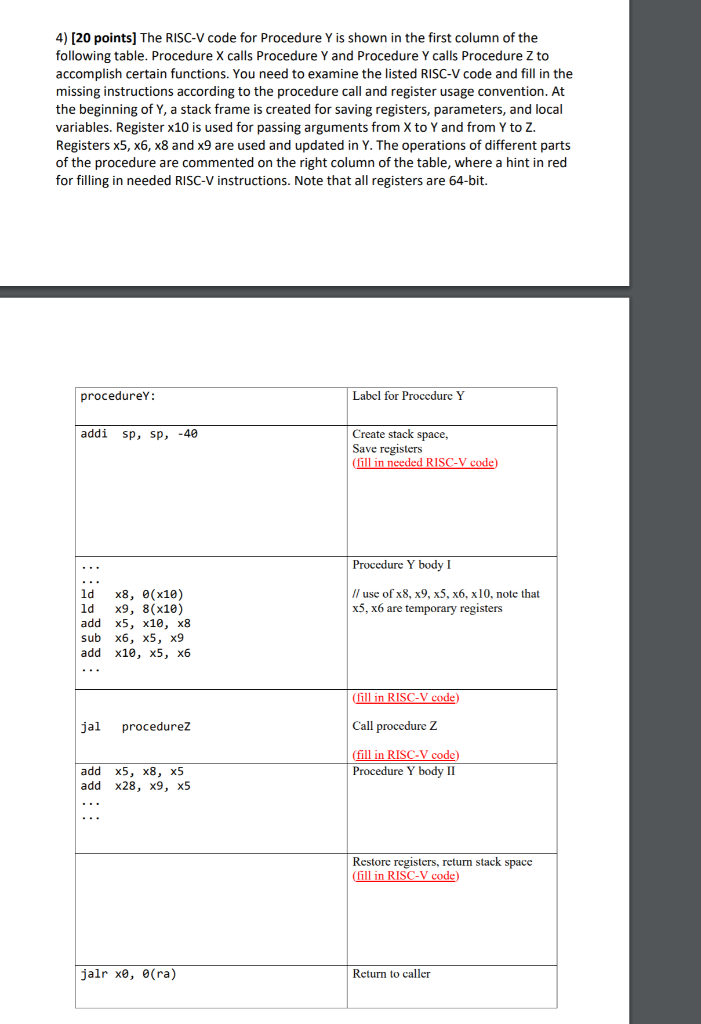
4) [20 points) The RISC-V code for Procedure Y is shown in the first column of the following table. Procedure X calls Procedure Y and Procedure Y calls Procedure Z to accomplish certain functions. You need to examine the listed RISC-V code and fill in the missing instructions according to the procedure call and register usage convention. At the beginning of Y, a stack frame is created for saving registers, parameters, and local variables. Register x10 is used for passing arguments from X to Y and from Y to Z. Registers x5, x6, x8 and 9 are used and updated in Y. The operations of different parts of the procedure are commented on the right column of the table, where a hint in red for filling in needed RISC-V instructions. Note that all registers are 64-bit. procedureY: Label for Procedure Y addi sp, sp, -40 Create stack space, Save registers Il in needed RISC-V code) Procedure Y body I Il use of x8, x9, X5, X6, x10, note that X5, X6 are temporary registers ld x8, (x10) ld x9, 8(x10) add x5, x10, x8 sub x6, X5, X9 add x10, X5, X6 (fill in RISC-V code) jal procedurez Call procedure Z (fill in RISC-V code Procedure Y body II add x5, x8, x5 add X28, x9, x5 Restore registers, return stack space (fill in RISC-V code) jalr x8, 8(a) Return to caller 4) [20 points) The RISC-V code for Procedure Y is shown in the first column of the following table. Procedure X calls Procedure Y and Procedure Y calls Procedure Z to accomplish certain functions. You need to examine the listed RISC-V code and fill in the missing instructions according to the procedure call and register usage convention. At the beginning of Y, a stack frame is created for saving registers, parameters, and local variables. Register x10 is used for passing arguments from X to Y and from Y to Z. Registers x5, x6, x8 and 9 are used and updated in Y. The operations of different parts of the procedure are commented on the right column of the table, where a hint in red for filling in needed RISC-V instructions. Note that all registers are 64-bit. procedureY: Label for Procedure Y addi sp, sp, -40 Create stack space, Save registers Il in needed RISC-V code) Procedure Y body I Il use of x8, x9, X5, X6, x10, note that X5, X6 are temporary registers ld x8, (x10) ld x9, 8(x10) add x5, x10, x8 sub x6, X5, X9 add x10, X5, X6 (fill in RISC-V code) jal procedurez Call procedure Z (fill in RISC-V code Procedure Y body II add x5, x8, x5 add X28, x9, x5 Restore registers, return stack space (fill in RISC-V code) jalr x8, 8(a) Return to caller
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


