Question: 5. Secure System Design (25 marks) In a privileged membership club, there are sole facilities provided for their members exclusively, such as restaurants and
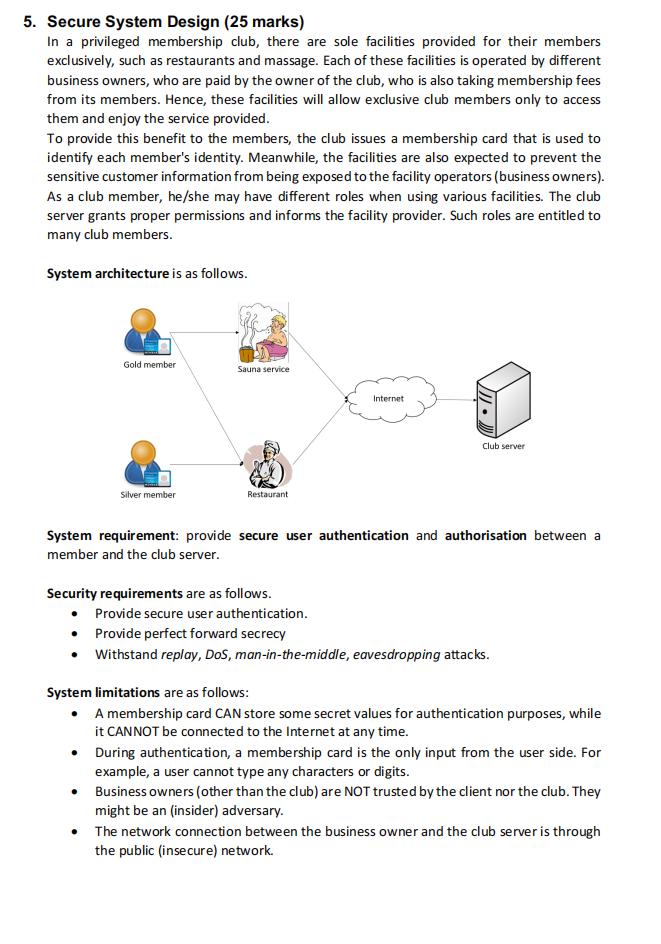

5. Secure System Design (25 marks) In a privileged membership club, there are sole facilities provided for their members exclusively, such as restaurants and massage. Each of these facilities is operated by different business owners, who are paid by the owner of the club, who is also taking membership fees from its members. Hence, these facilities will allow exclusive club members only to access them and enjoy the service provided. To provide this benefit to the members, the club issues a membership card that is used to identify each member's identity. Meanwhile, the facilities are also expected to prevent the sensitive customer information from being exposed to the facility operators (business owners). As a club member, he/she may have different roles when using various facilities. The club server grants proper permissions and informs the facility provider. Such roles are entitled to many club members. System architecture is as follows. Gold member Silver member Sauna service Restaurant Internet Club server System requirement: provide secure user authentication and authorisation between a member and the club server. Security requirements are as follows. Provide secure user authentication. Provide perfect forward secrecy Withstand replay, DoS, man-in-the-middle, eavesdropping attacks. System limitations are as follows: A membership card CAN store some secret values for authentication purposes, while it CANNOT be connected to the Internet at any time. The network connection between the business owner and the club server is through the public (insecure) network. During authentication, a membership card is the only input from the user side. For example, a user cannot type any characters or digits. Business owners (other than the club) are NOT trusted by the client nor the club. They might be an (insider) adversary. Your Task: Design a system to archive the system and security requirements. a. In order to establish secure communication, there are three phases: user authentication, authorization, and key establishment. In what order of these three phases should be conducted? (2.5 marks) b. What kind of information should be stored on a membership card for authentication? (2.5 marks) c. Design (a brief description) a security mechanism for key establishment and user authentication phases. The design should satisfy the security requirements if an item is applicable. Justify your answers. (15 marks) d. For user authorization, we may consider the access control models such as ACM, BLP, Biba and RBAC (role-based access control). Which one of the access control models would be better in this scenario? Why? (5 marks)
Step by Step Solution
There are 3 Steps involved in it
To meet the system requirements and security requirements while considering the system limitations we can design a secure authentication and authoriza... View full answer

Get step-by-step solutions from verified subject matter experts


