Question: . = 5) The network below uses the distance-vector routing algorithm. Assume the following: Links have the same cost in both directions. Nodes exchange their
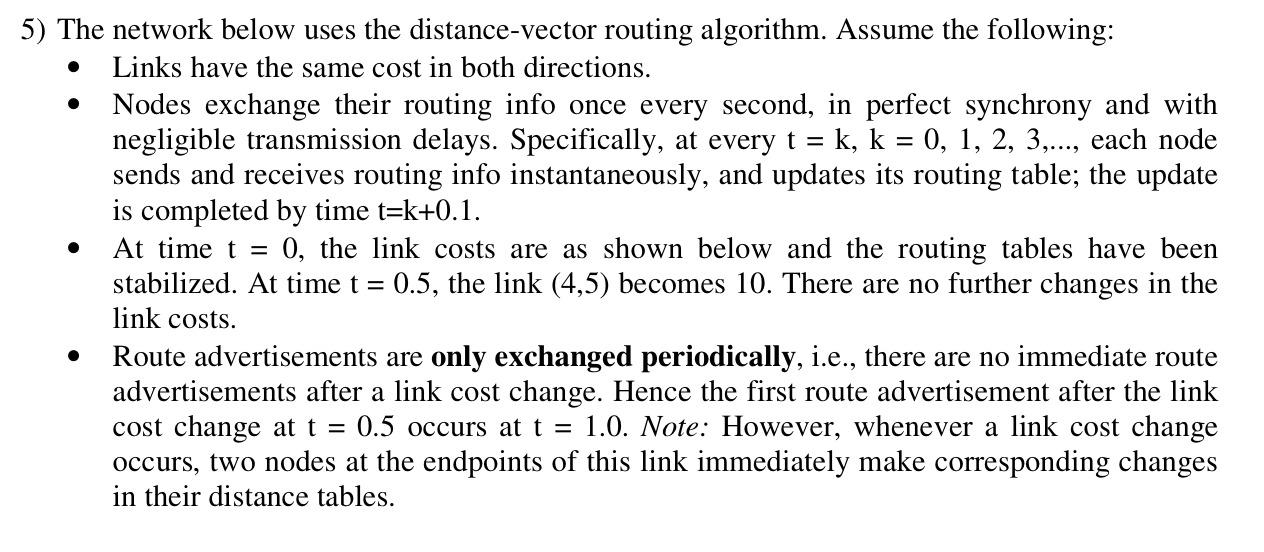
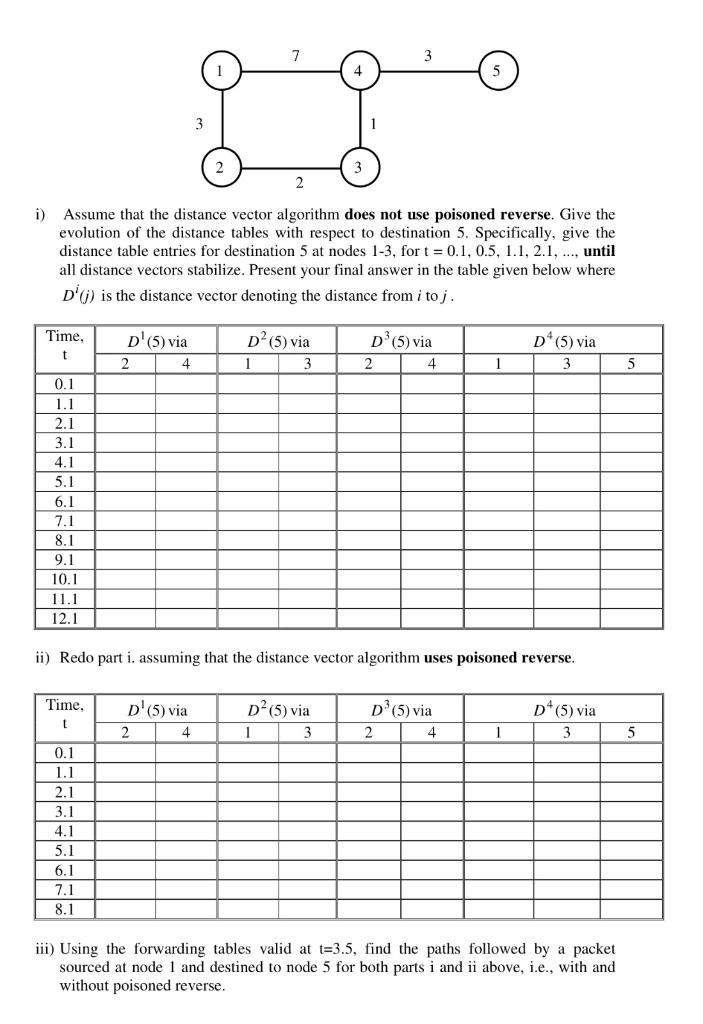
. = 5) The network below uses the distance-vector routing algorithm. Assume the following: Links have the same cost in both directions. Nodes exchange their routing info once every second, in perfect synchrony and with negligible transmission delays. Specifically, at every t = k, k = 0, 1, 2, 3,..., each node sends and receives routing info instantaneously, and updates its routing table; the update is completed by time t=k+0.1. At time t = 0, the link costs are as shown below and the routing tables have been stabilized. At time t = 0.5, the link (4,5) becomes 10. There are no further changes in the link costs. Route advertisements are only exchanged periodically, i.e., there are no immediate route advertisements after a link cost change. Hence the first route advertisement after the link cost change at t = 0.5 occurs at t = 1.0. Note: However, whenever a link cost change occurs, two nodes at the endpoints of this link immediately make corresponding changes in their distance tables. . 3 1 2 i) Assume that the distance vector algorithm does not use poisoned reverse. Give the evolution of the distance tables with respect to destination 5. Specifically, give the distance table entries for destination 5 at nodes 1-3, for t = 0.1, 0.5, 1.1, 2.1, ..., until all distance vectors stabilize. Present your final answer in the table given below where D'() is the distance vector denoting the distance from i toj. Time, t D'(5) via 2 4 D (5) via 3 D (5) via 2 4 D*(5) via 3 1 5 0.1 1.1 2.1 3.1 4.1 5.1 6.1 7.1 8.1 9.1 10.1 11.1 12.1 ii) Redo part i. assuming that the distance vector algorithm uses poisoned reverse. Time. t D'(5) via 2 4 D (5) via 1 3 D}(5) via 2 D(5) via 3 4 1 5 0.1 1.1 2.1 3.1 4.1 5.1 6.1 7.1 8.1 iii) Using the forwarding tables valid at t=3.5, find the paths followed by a packet sourced at node 1 and destined to node 5 for both parts i and ii above, i.e., with and without poisoned reverse
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


