Question: 64-bit input 64-bit output 32-bit L 32-bit Ly 32-bit Rn 32-bit _, _32-bit R Mangler Function Mangler Function K 32-bit loud 32-bit An:1 32-bit L:1)
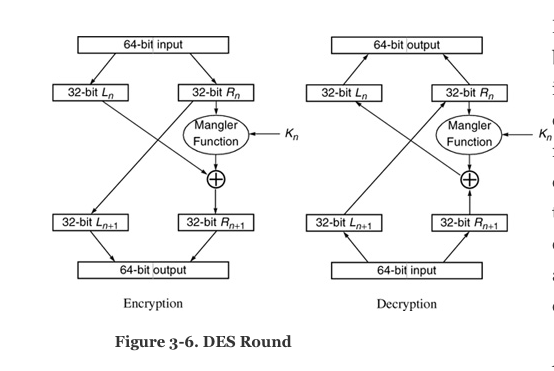

64-bit input 64-bit output 32-bit L 32-bit Ly 32-bit Rn 32-bit _, _32-bit R Mangler Function Mangler Function K 32-bit loud 32-bit An:1 32-bit L:1) 32-bit Anti 64-bit output 64-bit input Encryption Decryption Figure 3-6. DES Round Let L, R, K, denote 32-bit, 32-bit and 48-bit random numbers respectively, and let R (L, R., K) = (2x+1, R.+1) represent the DES encryption round shown in the left diagram in Figure 3.6 in the textbook, which has included 2 functional mappings: L, R, K, L (this means Le+1 is a function of L., R., K.) L, R, K, R.+1 (this means R.+1 is a function of L., R., K.) 1) Prove that R.(Rx+1, Lo+1, K.)=(R., L.) 64-bit input 64-bit output 32-bit L 32-bit Ly 32-bit Rn 32-bit _, _32-bit R Mangler Function Mangler Function K 32-bit loud 32-bit An:1 32-bit L:1) 32-bit Anti 64-bit output 64-bit input Encryption Decryption Figure 3-6. DES Round Let L, R, K, denote 32-bit, 32-bit and 48-bit random numbers respectively, and let R (L, R., K) = (2x+1, R.+1) represent the DES encryption round shown in the left diagram in Figure 3.6 in the textbook, which has included 2 functional mappings: L, R, K, L (this means Le+1 is a function of L., R., K.) L, R, K, R.+1 (this means R.+1 is a function of L., R., K.) 1) Prove that R.(Rx+1, Lo+1, K.)=(R., L.)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


