Question: 7. Security technologies - Secure tunnel (10%) (1) Refer to the diagram below. A VPN is created between two routers over the Internet. Answer the
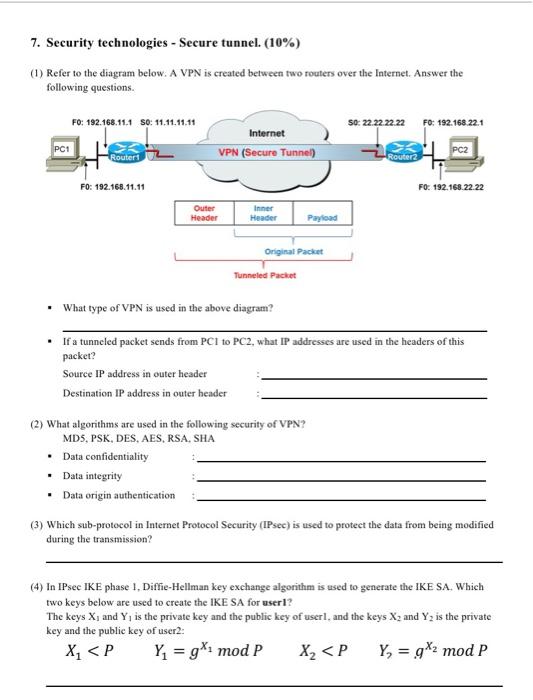
7. Security technologies - Secure tunnel (10%) (1) Refer to the diagram below. A VPN is created between two routers over the Internet. Answer the following questions. FO: 192.168.1.1 SO: 11.11.11.11 SO: 22.22.22.22 Fo: 192.168.22.1 PCI Internet VPN (Secure Tunnel) PC2 Router Router FO: 192.168.11.11 FO: 192.168.22.22 Outer Header Inner Header Payload Original Packet Tunneled Packet What type of VPN is used in the above diagram? If a tunneled packet sends from PCI to PC2, what IP addresses are used in the headers of this packet? Source IP address in outer header Destination IP address in outer header (2) What algorithms are used in the following security of VPN? MDS, PSK, DES, AES, RSA, SHA Data confidentiality Data integrity . Data origin authentication (3) Which sub-protocol in Internet Protocol Security (IPsec) is used to protect the data from being modified during the transmission? (4) In IPsec IKE phase 1, Diffie-Hellman key exchange algorithm is used to generate the IKE SA. Which two keys below are used to create the IKE SA for user? The keys X, and Y, is the private key and the public key of userl, and the keys Xz and Y2 is the private key and the public key of user2: X;
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


